Jawaharlal Nehru Technological University Kakinada 2010-1st Sem B.E Computer Science and Engineering Code No: V3126/R07 III B.TechSupplementary s, SOFTWARE TESTING METHODOLOGIES ( Common to C
Thursday, 08 August 2013 04:05Web
Page 1 of 2
Code No: V3126/R07 Set No. 1
III B.Tech I Semester Supplementary Examinations, May 2010
SOFTWARE TESTING METHODOLOGIES
(Common to Computer Science & Engineering and info Technology)
Time: three hours Max Marks: 80
ans any 5 ques.
All ques. carry equal marks
1. (a) Why is it impossble for a tester to obtain all the bugs in a system? Why might it not be necessary for a program to be completely free of defects before it is delivered to its customers?
(b) To what extent can testing be used to validate that the program is fit for its purpose? explain. [10+6]
2. (a) discuss with a suitable example how to convert a Multi-Exit routine to an equivalent single-exit routine.
(b) explain the path testing strategy for Multi-entry / Multi-exit routines. [8+8]
3. (a) explain the 3 possible interpretations of the decision symbol with 2 or more outlinks.
(b) What is meant by transaction flow structure? explain the reasons why the transaction flows are often structured? [6+10]
4. (a) What is meant by a nice domain? provide an example for nice two-dimensional domains.
(b) explain the subsequent terms: [8+8]
i. Linear domain boundarees
ii. Non linear domain boundaries
iii. Complete domain boundaries
iv. Incomplete domain boundaries
5. Using reduction procedure convert flow graph whose links are tagged into a path expression. discuss every step with flow graph shown in figure five (given with attachments). [16]
6. (a) discuss about the don?t care conditions in the logic based testing.
(b) discuss about the ambiguities and contradictions in the specifications. [16]
7. Write short notes on:
(a) Transition bugs
(b) Impact of bugs
(c) State bugs. [16]
8. (a) elaborate the disadvantages of array representations?
(b) explain the algorithm for finding set of all paths. [8+8]
9
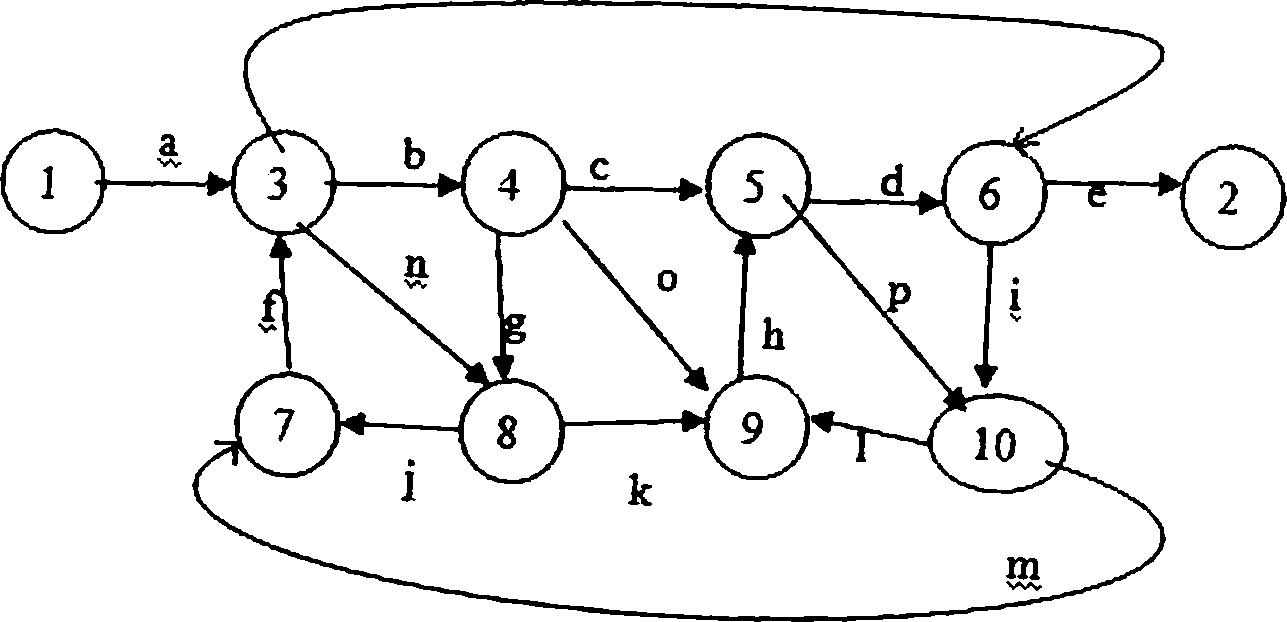 |
|
Figure 5 |
|
Attachment: |
| Earning: Approval pending. |
