University of Mumbai 2009 M.C.A Advanced Data Based Techniques - Question Paper
MCA Advanced Data Based Techniques
V-Ex-l-09-E-Scan-2
Hm '
V-Ex-l-09-E-Scan-2
OO ,(2
Advanced Dcttei Ba.secf 1 >
V-Ex-l-09-E-Scan-2
Con. 2476-09.
V-Ex-l-09-E-Scan-2
{3 Hours)
N.B. : (]) Question No. 1 is compulsory.
(2) Attempt any four from remaining six.
1. Explain the following : (Any four)
5
5
5
5
5
10
10
(a) Collaborating Servers
(b) Bayesian Networks
(c) Phantom Deadlock
(d) Temporal Databases
(e) OQL
2. (a) Explain different types of transparencies in DDBMS.
(b) Explain various OLAP implementation techniques.
3. (a) What is 3-phase commit protocol ? Give an example how it is different from 2PC 10
protocol.
(b) Explain ETL process in Datawarehousing. 10
4. (a) Describe association, classification and regression rules. What is the difference 10
between support and confidence of a rule ?
(b) What are the new kinds of data types supported in object database systems ? 10 Give an example of each type.
5. (a) Discuss deadlock detection in distributed database. Explain the various deadlock 10
detection approaches.
(b) Discuss with an illustration ORDBMS database design issues. 10
6. (a) Describe and differentiate between pipelined parallelism and data partitioned 10
parallelism.
(b) What is authorization graph ? Explain SQLs Grant and Revoke commands in terms 10 of their effect on this graph. Discuss what happens when users pass on privileges that they receive from someone else.
7. Compare and contrast the following :
(a) Distributed Databases and Centralized Databases
(b) Semi joins and Bloom joins
(c) Ol .TP and OLAP
(d) Log based and Procedural based implementation of Capture.
MCA StH-rg-M-cfitfOK'K AeCUVlty
(OLD COURSE)
IS**1
(3 Hours}
Cl) Question No 1 is compulsory
(2) Attempt any four form the remaining
C3) Figures to right indicate full marks
(4) Illustrate answers with sketches wherever necessary
(5) Answers to sub questions should be answered together.
What are Hash Algorithms? Discuss MD5 and compare it with SHA-1
Explain the procedure of Certificate Revocation
What is asymmetric key encryption? Discuss RSA with an example
Distinguish between a CA and KDC
What is authentication? Explain the different methods of authentication
What are firewalls? Explain its different types
10 10 10 10 10 10
Discuss the various PKI trust models 10
Explain the reflection attack with an example and explain how it 10 can be fixed
What is a digital signature? Explain the Digital Signature 10
Standard
How is the security of E-mail achieved 10
What is Kerberos ? Explain 10
Give an overview of DES. What are weak and Semiweak keys 10
Write short notes on any four of the following 20
1) El-Gamal Signatures 2} Virus
3) SSL
4) ECB and CBS mode of encryption
5) Smart Cards.
 |
|
BB-9258 |
Con. 2319-09.
(3 Hours)
[ Total Marks : 100
N.B. (1) Question No. 1 is compulsory.
(2) Answer any four questions from Question Nos. 2 to 7.
1. (a) What is Session Tracking ? Explain with suitable example.
10
(b) Write a program using JSP code which validates Registration form for email id, 10 user name, password, phone number. Email-id should contain @ and . And after. there can be two or three characters only, Telephone number should have 8 digits, Password should be 8 characters containing alphabets and numbers only.
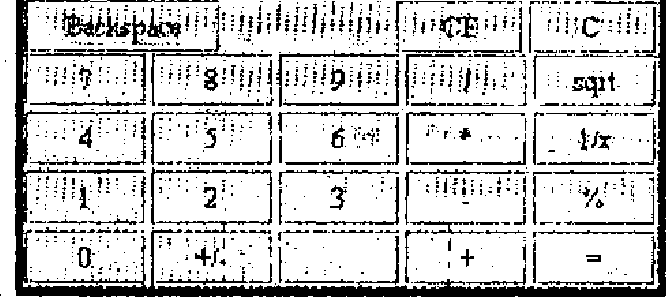
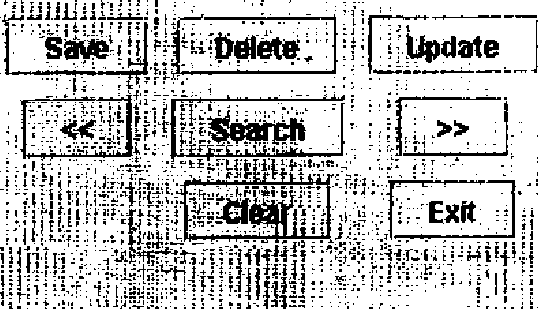
2. (a) Write code to display following GUI with appropriate swing components : 10
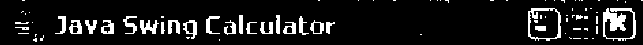 |
|
FOr Help |
|
S |
 |
(b) Create a swing GUI which accept any number from user and print triangle for 10 that number.
5
5 4 5 4 3 5 4 3 2 5 4 3 2 1 5 4 3 2 5 4 3 5 4 5
3. (a) List all properties of Java Beans. Explain any two of them with suitable example 10
(program).
(b) What are the advantages of JavaBean ? Explain with example the role of manifest 10 and jar file.
4. (a) What are the Servlets ? What are the advantages of Servlets ? Explain the 10
life cycle of Servlets.
(b) Write a code of a Servlet that uses cookies to store the number of times a user 10 has visited your servlet.
5. (a) Explain Statement, Prepared Statement and callable statement.
(b) Explain different types of joins with simple example.
6. (a) List out all JSP objects and explain them in short with their scope.
(b) Explain exception handling in JSP along with example.
7. Create a simple address book that keeps Names, email, Address and Phone Numbers of people using java swing (use GridBagLayout) and use JDBC driver and SQL statements for connecting and manipulating with the database.
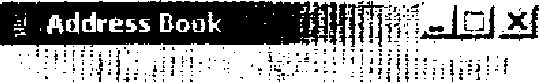

|
pw* r |
 |
J
OR
7. (a) Write a program to set and read cookies in a JSP.
(b) Develop your own Bean and write down the steps to add it in Tool Box of BDK.
|
Attachment: |
| Earning: Approval pending. |
