University of Mumbai 2009 M.Sc Information Technology M Sc Software Testing and Information Security - Question Paper
M Sc Software Testing and info Security
-09.
feftPPlL 2&c
MSc-Tt part-1C
Pa.pct -X
SdHxmmc. ~Ps&\ir CVM XoVormaJion Sccut ilR-gi 44 (3 Hours) [Total Marks : 75
1) Attempt any five questions but not more than three from any section
2) Figures to the right indicate full marks.
3) Answers to the two sections must be written in separate answer books and should be submitted separately.
4) Each question carries 15 marks.
Section-I
List all the component of software development process and explain in brief. List and explain all the steps in selecting appropriate testing tool,
OR
Write a short note on developing a test strategy. 7
Discuss all the issues which are causing the organization to revise the approach 8 for testing.
Explain the concept of application fit.
How to select the best test team? Explain in brief.
OR
Write a short note on functional system testing techniques. 7
List all the eleven steps of software testing process and explain the second step 8 in detail.
List all the concerns of testing in multiplatform environment.
With the help of the workbench explain the process of testing a web based system.
OR
With the help of the workbench explain the process of testing a off the shelf 7 software.
List and explain the concern of testing client/server systems. 8
Q7 a) Why do we need security? Explain in detail about the various types of security mechanisms
b) Write a note on:
i) Brain virus
ii) Trapdoors
OR
Q8 a) Describe the following :
i) Base/Bound Registers
ii) Segmentation
b) Define inference problem. Explain the various ways to infer the sensitive data from the database
Q9 a) Define the following:
i) Intrusion Detection System
ii) Biba Integrity model
b) What makes a network vulnerable? Explain the architecture of network security control
OR
Q10 a) Describe the security features of operating system and explain method of separation
b) Explain the various file protection mechanisms available
Qll a) Describe the ways in which integrity lock and sensitivity lock differs with an example
b) State the factors involved in planning of security for any system
OR
Q12 a) State the reason for having cyber crime as a separate crime. Describe copyright law associated with that.
b) What is risk analysis and explain the steps in risk analysis
Par-;m_ PPDC 2SHvl. icocj T'bHK) 4 PS
Con. 1633 & (a), (b)-09. PSP & EH CR-8070 to 8072
(3 Hours) [Total Marks : 75
1. Attempt any FIVE questions but not more than THREE questions from any section.
2. Answers to the two sections must be written in separate answer books and should be submitted separately.
3. Draw necessary figures wherever required.
4. Each question carries 15 marks.
Section I
Q.l A What is cache coherence? How to avoid it? Explain with example. 7
B Write a note on Shared and Distributed memory multiprocessing. Compare both. 8
OR
Q.2 A Write a short note on pipeline processors. 7
B Write a short note on: i) Time shared ii) Cross bar switch 8
Q.3 A Write a short note on tree structured barrier. 7
B Write a short note on: i) Odd even transposition sort ii) Block sorting algorithm. 8
OR
Q.4 A Write a short note on Occam. 7
B List the conditions for SMP program to give the same output in repeated 8 executions.
Q.5 A Write a short note on simple model of speedup. 7
B An application running on 8 processors spends 2% of its time in serial code. What 4 is the scaled speedup of the application?
C Explain the importance of shared memory variables in parallel processing. 4
OR
Q.6 A Explain operation of cache. 7
B 30% of a programs execution time is spent within inherently sequential code. What 4 is the limit to the speedup achievable by a parallel version of the program?
C State the Karp Flatt Metric. 4
[ TURN OVER
Explain how microkernels can be used to organize an operating system in a client-server fashion.
Explain what is an object adapter. Mention some design issues for an object adapter that is to support persistent objects.
OR
What is the difference between a distributed operating system and a network operating system? .
Explain the principle of a token bucket algorithm.
Explain Two phase commit and Three phase commit protocol in detail.
How concurrency control can be achieved using timestamps? Explain with an example.
OR
Consider a Web browser that returns an outdated cached page instead of a more recent one that had been updated at the server. Is this a failure, and if so, what kind of failure?
What is client - centric consistency? Give an example where client-centric consistency can easily lead to write-write conflicts.
Explain the different components in SESAME.
Discuss the side effects in Codas RPC2 system.
OR
Explain in short what is xFS system? Discuss the main data structures used in xFS system?
Assume a Globe object server has just installed a persistent local object. Also, assume that this object offers a contact address. Explain Why that address be preserved when the server shuts down? .
1) Attempt any five questions but not more than three from any section.
2) Figure to the right indicate full marks.
3) Answers to the two sections must be written in separate answer books and should be submitted separately.
4) Each question carries 15 marks
Q.l A Describe the Fully observable, Deterministic, Static, and Single agent task 08 environments giving an example of each.
B Describe the design and working of a learning agent with suitable diagram. 07
Q.2 A Discuss the searching with partial information with reference to the OK Sensorless, Contingency, and Exploration problems.
B State Rumania problem. Discuss the problem with the help of greedy best- 07 first scarch technique.
Q.3 A Define wumpus world problem. State its PEAS description. Describe 08 characteristics of the wumpus world with reference to different task environment.
B Explain alpha-beta pruning. Explain with example how does it overcomes 07 the drawbacks of Minimax algorithm.
Q.4 A Briefly explain what do you mean by knowledge engineering? State and 08 explain steps involved in knowledge engineering
B Write a short note on following: 07
i) Quantifiers
ii) Unification
Q.5 A Explain following with suitable example 08
i) Conditional probability
ii) Prior probability,
B Compare STRIPS and ADL language used for representing planning 07 problem. Explain with example.
Q.6 A Explain the characteristics of single layer and multilayered feed- forward 07 neural network.
B Discuss applications of an intelligent system in real world. 05
C Define Intelligence. 03
[ TURN OVER
q 7 (a) Describe the McCulloch and Fitts model of neural network. What are its
advantages and disadvantages?
(b) List and explain different types of neural network architectures.
(c) Write short note on Learning rules. .
OR
Q.8 (a) Explain the least mean square algorithm in detail.
(b) Write a note on knowledge representation schemes.
(c) What is spurious state? Explain.
q 9 (a) state the significance of hidden layers in modeling of neural network for learning.
Describe the Boltzmann learning machine. What are its salient features.
(b)
(c)
Explain different types of activation function in neural network.
O 10 (a) Explain the error-correction learning mechanism in neural network.
Briefly describe the Hopfield networks with reference to energy function and
(b)
error performance.
(c) Define Fuzzy set.
Q.l'l (a) What are fuzzy systems? List and explain at least four applications of fuzzy systems.
(b) What is defuzzification? What are its applications?
(c) Write a note on membership functions.
OR
Q.12 (a) What are fuzzy controllers? Describe with example.
(b) State and explain extension principle.
(c) Write a note on fuzzy measures.
Con. 1633 (b)09.
(3 Hours)
N.B. 1. Attempt any FIVE questions but not more than THREE questions from any section.
2. Answers to the two sections must be written in separate answer books and should be submitted separately.
3. Write answers to same question together.
4. Each question carries 15 marks.
SECTION -1
a. What are linear discrete time shift invariant systems? Consider the linear discrete time 7 shift invariant system with unit sample response
h(n) = (j) u(n) where j =
Determine the steady state response i.e. the response for large n to the excitation
x(n) = [cosrrn]u(n)
Determine the z-transform including the region of convergence for each of the following sequences: i- - 1)
b.
ii. S(n 1)
iii. )n[u00 - u(n ~ 10)]
fl! 0 < lal < 1
iv.
OR
Explain the following properties of Discrete Fourier Series i. Linearity
2. a.
Shift of a sequence Periodic convolution Symmetry
n.
iii.
iv.
Determine the sequence x(n) whose z-transform is X(z) = ez + ez, z * 0. Determine the z-transform of n2x(n) in terms of the z-transform of x(n).
a. Explain the Goertzel algorithm to compute Discrete Fourier Transform.
b. Discuss in detail the design of Infinite Impulse Response filter.
OR
a. Explain the Decimation - in - time FFT algorithm to find DFT.
b. Explain any eight properties of Discrete Fourier Transform.
Explain in detail the DSP processor TMS 320C40/50.
Compare IIR and FIR digital filters.
OR
Consider a continuous time system with system function
s + a
WaCs)-(s +'a) + f>2 Determine the system function H(z). i.e the z-transform of unit sample response) of a discrete system designed from this system on the basis of:
i. Impulsive invariance i.e. k(n) = kn(nT)
ii. Step variance i.e.
s(n) = sa(nT) where s(n) ==-.*(k) and sa(t) = f*ha(T)dT
State the different applications of digital signal processing. Explain any two in detail.
Scctiim - II
a Write notes on: . . .
i.Microwave Transmission ii. Effect of noise on communication.
b Discuss the characteristics of Transmission mediums.
OR
a Write notes 011:
i. Time Division Multiplexing
ii. Frame Format.
b Explain the working of IBM Token Ring.
a Write notes on:
i. Forward addressing in WLAN
ii. Virtual Private Network.
b Explain how LAN Hardware filters the packet.
OR
a What are contention protocols? Describe the CSMA / CD technique, b Explain the structure of a Routing Table and explain with example how is it used for path computation in network.
a Write notes on:
i.X.25 ii.Frame Relay
b Explain the structure of a routing table and explain with example how it is used foi path computation in a network.
OR
a Write notes on:
i. Local Talk
ii. Multicast Networks
b How to avoid Network Congestion.
f-rr
I'/-1 Gl V~0 ni > -Tv"
1 M & C IJ -r (3 Hours)
Con. 1634 & {a), (b)-09.
2 H1 ?oo, CR-8076 to 8078
[Total Marks : 75
WB 1) Attempt any five questions but not more than three from any section
2) Figure to the right indicates full marks. , , , ,,
3) Answers to the two sections must be written in separate answer books and should be
submitted separately.
4) Each question carries 15 marks
Section -1
08
07
07
08
07
08
07
08
07
08
08
07
Q. 1 (a) Explain in detail any two applications of pattern recognition system. Outline the design out the recognition system for both.
(b) Discuss the use of discriminant functions and decision surfaces in analysis and interpretation of patterns.
Or
0.2 (a) Describe the Hidden Markov Mode! for estimation and recognition problem.
(b) Explain the concept of Parzen windows as nonparametric method for pattern recognition and decision making.
q 3 (a) Explain the issues with minimizing the perception criterion function m
discriminant analysis. . .
(b) Outline and explain the features of Bayes decision theory and their use m
recognition systems.
Or
Q.4(a) Explain how" we can use decision trees and grammatical methods in recognition of patterns?
(b) Write short note on
i. CART
ii. Nearest-Neighbor Rule
Q.5 (a) What is classification problem? What is the impact of re-sampling on estimation and classifier design?
(b) Write a short note on
i. Hierarchical clustering-ii Maximum likelihood estimation.
r
Q.6 (a) Discuss the role of unsupervised learning in pattern recognition systems. What are the advantages and disadvantages of the methodology as compared to supervised learning?
(b) What are the challenges faced by modern pattern recognition systems.'1 Explain,
Q. 7 (a) Describe the labeling algorithm in determining the connected components for
recognition of shapes. .
(b) What is segmentation? Explain different types of segmentation techniques
used in machine vision.
OR
Q.8 (a) What is spatial clustering? Outline its advantages and disadvantages.
(b) Write a short note on
i. Least-square fitting
ii. Hough transform
Q,9 (a) Outline the theory behind drawing lines. . .
(b) Explain the inverse perspective projection in viewing and recognition ot
objects.
(c) What are spatial moments?
OR
Q. 10 Compare local and global features of object representation in matching
(a) problem.
(b) What is region growing? Explain with example.
(c) What is photometry? Explain.
Q.l 1 Explain the following with reference to area extraction
(a) i. Hough Transform
ii. Curve fitting
(b) Write a detailed note on Model database organization.
OR
Q.l2 What is view class matching? Explain the concept using suitable example.
(b) Write a detailed note on knowledge-based vision.
H S 1) Attempt any five questions but not more than three from any section
2) Figure to the right indicate full marks.
3) Answers to the two sections must be written in separate answer books and should be submitted separately.
4) Each question carries 15 marks
SECTION -1
Q1 a) Describe the hardware and software vulnerabilities
b) What are the requirements for a malicious attacker?
Q2 a) How to solve the flaws of synchronization?
b) Explain the working of AES cryptographic algorithm. >
. O
Q3 a) What are the causes and effects of viruses?
b) Explain the process of identifying Potential Covert channels
Q4 a) What are the methods of fixing flaws in the authentication process? 8 b) Explain the multiple virtual memory spaces and virtual machines 7
Con. 1634 (a)-CR-8077-09. 4
Section - II
Q. 7 a Write note on: i. Immersion ii. Color Space
b Discuss the classification of Virtual Reality (VR) systems.
OR
Q. 8 a Explain the process of Extrusion.
b Write note on Bezier Space Curves.
Q. 9 a Discuss the classification of Virtual Objects, b Explain in brief linear interpolation.
OR
Q. 10 a Discuss the simulation of objcct falling in a gravitational field, b Write note on : Tracking sensors.
Q. 11 a Explain the simulation of Steerable wheel..
b List the steps involved in exhibiting steady state behavior.
OR
Q. 12 a Discuss the advantages of working in virtual domain.
b How Virtual Reality is useful in Military training? Explain.
1. Attempt any FIVE questions but not more than THREE questions from any section.
2. Answers to the two sections must be written in separate answer books and should be submitted separately.
3. Write answers to same question together.
4. Figures to the right indicates full marks
5. Each question carries 15 marks.
Section I
1 A Write a short note on Multimedia communication for healthcare. 7 B Define: 8
1. Multimedia system
2. Continuous media
3. Multimedia Computing
4. Multimedia Communication
t
OR
2 A Write different approaches to providing QOS guarantees in high- 7
speed n/w.
B What is audible frequency range? Why the speech signal is 8
measured in decibels (dB)? Discuss for ideal sinusoidal waveform
.3 A What is composite format? List and explain all composite video 7 formats.
B Why image and digital video compression is required? What are 8 the key parameters need to be considered? What is lossy and lossless compression?
OR
4 A List all the video performance measurements and explain any two. 7 B Write a short note on bitstream architecture 8
5 A Discuss the limitations of current operating system. What extra 7
things should be added to support distributed continuous media applications?
B What is XIE? Explain with diagram 8
. OR
6 A List and explain the barriers to widespread use and success of 7
authoring and presentation systems B List and explain the file format techniques for supporting real time 8
interchange [TURN OVER
a) What are packages? How will you create package in java. Create 7 two classes in packages and demonstrate to use that.
b) Write a Code for bouncing string .Multiple strings should be 8 displayed in different colors. The algorithm for bouncing each string must be assigned to different threads
- OR
a) With the help of a neat diagram, explain the three active document 7 representations and the programs that translate the document.
b) Write a code in java to copy a file to another file. 8 e.g java filesource filedest
a) Explain Java Security Framework. 7
b) Explain Security Policy of Java Browser 8
OR
a) Write a note on Remote Procedure Call Paradigm. 7
b) Explain MIB object names and various MIB variables. 8
a) What is Java Media Framework? How will you create Media 7 Player? And how will you add the player to you application.
b) Explain Instrument, Protocol and Operation cassettes classes used in 8 Java
OR
a) Difference between JavaScript and Java? Explain the properties and 7 methods of document object used in JavaScript,
b) How will you create objects in Java and how will you call Java 8 COM objects from Visual Basic & Excel.
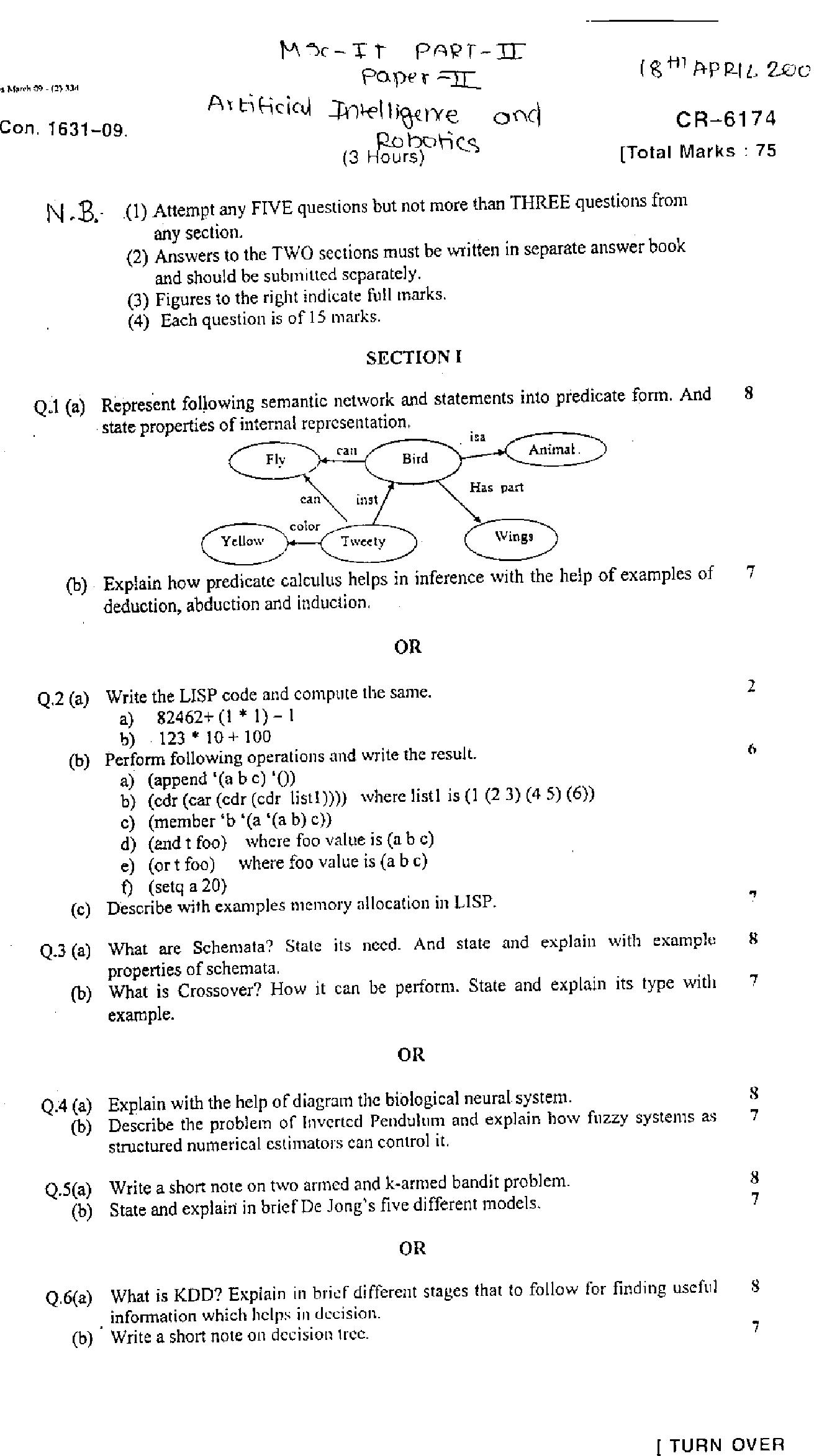
Q 7 (a) Explain features that distinguish soft automation from hard automation.
(b) State and explain different types of joints.
(c) Describe robot specification with the help of following points:
(i) Reach and Stroke
(ii) Tool Orientation.
OR
Q:8 (a) Consider the single-axis robot as shown in the diagram, which corresponds to 0 =
' 7t/2' . M T
Suppose the point p on the mobile link has coordinates [p] - [0.5, 0.5,2.0]
i) Find an expression for R(9), the corresponding transformation matrix which maps mobile M coordinate into fixed F coordinates as a function of joint variable 0 .
ii) Use R(0) to find [p]F when 0 = n and 9 = 0.
|
P. mJ Revolute |
|
- Mobile link |
f'd
(b) With the help of diagram explain screw transformation and Inverse screw
. transformation. .
Q.9 (a) Explain pick and place operation with the help of following points
a) Pick and Lift-Off points
b) Place and Set-Down points
c) Speed Variation. #
(b) State and explain Dcnavit-Hartenberg representation algorithm m detail.
OR
Q. 10(a) Explain working of Swell operator. State how it overcome limitations of slirink operator.
(b) Describe with example need of back lighting and front lighting in robot vision. Q.ll(a) The position and orientation of the camera relative to the robot base are specified by
the following matrix T were
' 0 -1 0 30'
-10 0 20 0 0 -1 15
tzt =
0 0 0 1
If the effective focal distance is f = 1 cm, find the coordinate of the image of the origin of the base frame of the robot with respect to the camera frame.
(b) What is mean by Compliant motion? Illustrate the same with suitable example.
OR
Q.12(a) Write a short note on straight line motion of the robot with the help of Taylor s algorithm.
(b) Explain the Euler number and its use in image processing. Explain the skeleton and bulk operators, break and bridge faults with neatly labeled diagrams.
|
Attachment: |
| Earning: Approval pending. |
