The Institute of Chartered Financial Analysts of India University 2010 C.A Chartered Accountant Integrated Professional Competence (IPCC) Revision Test s- 7A- Information Technology - Question Pa
May 2010: The Institute of Chartered Accountants of India - Revision Test ques. papers (RTPs) Integrated Professional Competence Course (IPCC) Examination: Paper 7A- info Technology: May 2010 University ques. paper
PAPER - 7 : INFORMATION TECHNOLOGY AND STRATEGIC MANAGEMENT SECTION A : INFORMATION TECHNOLOGY QUESTIONS
1. Define the following terms briefly:
|
(i) |
Power Supply Connectors |
(ii) |
SCSI |
|
(iii) |
Server |
(iv) |
Text Editors |
|
(v) |
Virtual Memory |
(vi) |
Word Processor |
|
(vii) |
String |
(viii) |
Referential Integrity |
|
(ix) |
Linked List |
(x) |
Mirror Log |
|
(xi) |
|
(xii) |
Client / Server networks |
|
(xiii) Site Blocking |
(xiv) |
Algorithm | |
(xv) Electronic Purse
2. Convert the following from one number system to another number system along with the working notes:
(i) (0 0 0 0 1 0 1 1) 2 = ( )10
(ii) (603)10 = ( )2
(iii) (149.50)10 = ( )2
(iv) (01101. 1100)2 = ( )10
3. Give one or two uses of each of the following:
(i) Cache Memory (ii) Touch Screens
(iii) OCR
(vi) Bluetooth
(ix) ISDN
(xii) EDI
(iv) Spreadsheet (v) DBMS
(vii) Program Documentation (viii) Modem
(x) Internet (xi) Web Casting
4. Distinguish between the following:
|
(i) |
Video Cards and Network Cards |
|
(ii) |
CRT and Flat-Panel |
|
(iii) |
File Manager and Query Manager |
|
(iv) |
Candidate Key and Alternate Key |
|
(v) |
DDL and DML |
(vi) Online Backup and Offline Backup
(vii) Synchronous Transmission and Asynchronous Transmission
(viii) Analytical CRM and Collaborative CRM
(ix) SET and JEPI
(x) Strategic SCM and Operational SCM
(xi) Program Design and Program Coding CLASSIFICATION OF COMPUTER
5. (a) Discuss the various categories of computers as per their size.
(b) How workstation differs from minicomputers?
COMPONENTS OF COMPUTER SYSTEM
6. (a) Discuss briefly Central Processing Unit with the help of a diagram.
(b) Discuss various features of CPU.
7. (a) Discuss the various Direct Data Entry devices.
(b) What are the advantages of Image Processing?
8. What is a programming language and discuss various categories of programming language?
9. (a) Discuss the purposes of application software.
(b) Discuss the importance of ERP.
10. Give some examples of DSS in accounting.
11. (a) Discuss the example-based, rule based, and frame based components of Expert
System.
(b) What benefits are offered by Expert System?
12. (a) Explain the management problem of file processing.
(b) Discuss the classification of DBMS users.
13. Discuss the various steps in developing a backup and recovery strategy.
14. (a) Discuss the different methods of storing data in a data warehouse.
(b) Mention the various concerns in using data warehouse.
15. (a) How can a computer network help in business?
(b) Explain the various data transmission techniques.
16. (a) Mention the various business uses of Internet.
(b) Which business activities are impacted by e-Commerce?
CUSTOMER RELATIONSHIP MANAGEMENT
17. (a) What are the needs of a good CRM program?
(b) What are the features of a technically functional CRM?
18. (a) What are the concerns that the business house has to address before initiating
electronic commerce?
(b) Discuss the various approaches of encryption.
19. A company has 2,500 employees. Their salaries are stored as J(s), 1, 2, ---- 2500. The salaries are divided in four categories as under:
(i) Less than Rs. 1,000 (ii) Rs. 1,000 to Rs.2,000
(iii) Rs. 2,001 to Rs. 5,000 (iv) Above Rs. 5,000.
Draw a flow chart for finding the percentage of the employees in each category.
20. A hire-purchases scheme has adopted the following criterion for its customers. The customers will get the credit facility if they satisfy any of the following conditions:
(i) The customer must hold the present job for more than 5 years and reside in the same place at least for 3 years. In this case, the customer will get credit up to rupees three thousand.
(ii) The monthly salary of the customer must exceed rupees two thousand and must hold the present job for more than 5 years. In this case credit will be given up to rupees four thousand.
(iii) The monthly salary must exceed rupees two thousand and reside at the same place at least for 3 years. In this case credit will be given up to rupees four thousand.
(iv) In the case, the customer's monthly salary exceeds rupees two thousand, holds the present job for more than 5 years and also reside in the same place at least for the 3 years, the credit facility will be up to rupees five thousand.
The credit facility is rejected for all other customers. Prepare a decision table for this
hire-purchase scheme.
1. (i) Power Supply Connectors allow the user to connect the power supply unit to the motherboard and provide power for the functioning of the various components that fit onto the motherboard.
(ii) SCSI stands for Small Computer System Interface which is a device interface used to solve the problem of a finite and possibly insufficient number of expansion slots.
(iii) Server is a computer system that provides services to other computing systems called clients / workstations / nodes over a network.
(iv) Text Editors are programs that allow text in a file to be created and modified and are especially useful to professional programmers.
(v) Virtual Memory, sometimes called virtual storage, extends primary memory by treating disk storage as a logical extension of RAM.
(vi) Word Processor is a computer application used for the production (including composition, editing, formatting, and possibly printing) of any sort of printable material.
(vii) String is a data type consisting of a sequence of contiguous characters that represent the characters themselves rather than their numeric values and includes letters, numbers, spaces, and punctuation.
(viii) Referential Integrity is a feature provided by Relational Database Management Systems (RDBMS) that prevents users or applications from entering inconsistent data.
(ix) Linked List is a group of data records arranged in an order, which is based on embedded pointers. An embedded pointer is a special data field that links one record to another by referring to the other record.
(x) Mirror Log is an optional file having extension .mlg, which is a copy of a transaction log and provides additional protection against the loss of data in the event the transaction log becomes unusable.
(xi) Email enables staff in the office to communicate with each other quickly and effectively and also provides capabilities for contact management, scheduling and task assignment.
(xii) Client / Server networks comprise of servers, typically powerful computers, running advanced network operating systems and user workstations (clients), which access data or run applications located on the servers.
(xiii) Site Blocking is a software-based approach that prohibits access to certain Web sites that are deemed inappropriate by management.
(xiv) Algorithm is a specific procedure that exists as a finite list of instructions specifying a sequence of operations to give answer to any problem of a given type.
(xv) Electronic Purse is yet another way to make payments over the Internet which is very similar to a pre paid card and can be used as a ATM card as well as a credit card.
2. (i) (0 0 0 0 1 0 1 1) 2 = (
)10
0 x 27 + 0 x 26 + 0 x 25 + 0 x 24 + 1 x 23 + 0 x 22 + 1 x 21+
1 x 20
0
0 + 8 + 0 + 2 + 1
+
+
= 0 + 0 Thus, (0 0 0 0 1 0 1 1) 2 = (11)10
|
(603)1 | ||||||||||||||||||||||||||||||
| ||||||||||||||||||||||||||||||
|
Thus, (603)10 (1 0 0 1 0 1 1 0 1 1)2 |
(
)2
Remainder
(iii) (149.50)io = ( )2
We have to solve the integral and fractional part separately. Consider integral part 149
Remainder
|
2 |
149 | |
|
2 |
74 |
1 |
|
2 |
37 |
0 |
|
2 |
18 |
1 |
|
2 |
9 |
0 |
|
2 |
4 |
1 |
|
2 |
2 |
0 |
|
2 |
1 |
0 |
(149) 10 = (1 0 0 1 0 1 0 1)2 Now consider fractional part 50.
(1)
Integer part
0.50 x 2
100 1
--
(0.50)10 = (1)2 (2)
Thus combining (1) and (2), we get,
(149.50)10 = (1 0 0 1 0 1 0 1. 1)2
(iv) (01101.1100)2 = ( )10
= 0 x 24 + 1 x 23 + 1 x 22 + 0 x 21 + 1 x 20 + 1 x 2-1 + 1 x 2-2 + 0 x 2-3 + 0 x 2-4
= 0 + 8 + 4 + 0 + 1 + 1/2 + 1/4 + 0 + 0
= 13 + 3/4 Thus, (01101. 1100)2 = (13.75)10
3. (i) Cache Memory is a special type of internal memory used by many central processing units to increase their performance or "throughput". Some of the information in the main memory is duplicated in the cache memory, which is slightly slower but of much greater capacity than the processor registers, and faster but much smaller than main memory. Multi-level cache memory is also commonly used
- "primary cache" being smallest, fastest and closest to the processing device; "secondary cache" being larger and slower, but still faster and much smaller than main memory.
(ii) Touch Screens are used in information-providing systems. These interfaces are also used in travel agents offices to display the names and addresses of all hotels, restaurants, and other places of interest, at a desired destination. Touch screens are also used in stock exchanges where buying and selling of stock is done.
(iii) OCR stands for Optical Character Reader which can read printed as well as handwritten documents. It eliminates the human effort of transcription. Since documents have only to be typed or handwritten, not very skilled staff (like the keypunch operators) is required. OCR characters can be sent as input to the CPU.
(iv) Spreadsheet programs help in managing the data in various formats and also increase the productivity when dealing with various types of data. Spreadsheets can be used to calculate balance sheets, profit and loss accounts and cash books. User can also perform bank reconciliation; calculate jobs costs, taxes, schedule payments, forecast profits and control stocks.
(v) DBMS stands for Database Management System. It is the tool that computers use to achieve the processing and orderly storage of data. Each piece of information can be added to a data base by using Database Management System and can be extracted later in a meaningful way in a wide variety of ways.
(vi) Bluetooth is a technology which enables the user of cellular phones, pagers, and Personal Digital Assistants (PDAs) to buy a three-in-one phone that can double as a portable phone at home or in the office. They can get quickly synchronized with information in a desktop or notebook computer, initiate the sending or receiving of a fax, initiate a print-out, and, in general, have all mobile and fixed computer devices be totally coordinated.
(vii) Program Documentation helps the user to diagnose any subsequent program errors, modifying or reconstructing a lost program. It specifies what the program is supposed to do-input, output, file layout, flowcharts, etc. which helps the auditors in future to study the project.
(viii) Modem stands for Modulator/Demodulator, which is an encoding as well as decoding device used in data transmission. Modems are used for handling data streams from a peripheral device to the CPU and vice versa through the common carrier network. It confers the ability to access remote computers and allows many employees to work at home and still have access to the computer system at the office.
(ix) ISDN stands for Integrated Services Digital Network. It is a system of digital phone connections to allow simultaneous voice and data transmission across the world. ISDN allows multiple digital channels to be operated simultaneously through the same regular phone cable meant for analog signals. With ISDN, it is possible to combine many different digital data sources and have the information routed to the proper destination.
(x) Internet helps in communication and meaningful data retrieval where the data is compiled from various sources and put together in a usable form. Business companies can grow by taking advantage of the efficient nature of low-cost advertising and commerce through the Internet, which is called e-Commerce.
(xi) Web Casting allows users to passively receive broadcast information rather than actively search the Web for information. Users can download software, select the frequency with which they will receive services, and subscribe to a variety of information sources.
(xii) EDI stands for Electronic Data Interchange. It is computer-to-computer communication using a standard data format to exchange business information electronically between independent organizations. Users can transmit business documents such as purchase orders, price quotes, shipping notices, and even payment orders electronically to customers and suppliers. Design documents, electronic funds transfers, and database transactions can all come under the EDI umbrella.
4. (i) Video Cards and Network Cards
Video Cards allow computers to display video and animation. Some video cards allow computers to display television as well as capture frames from video. A video card with a digital video camera allows computer users to produce live video. A high speed or network connection is needed for effective video transmission.
Network Cards allow computers to connect together to communicate with each other. They have connections for cable, thin wire or wireless networks.
CRT stands for Cathode Ray Tube, which uses a large tube-type element that looks like the picture tube in a standard TV set. Inside the tube is a gun that lights up the phosphorescent pixels on the screen surface. Although CRT technology is relatively inexpensive and reliable, CRT-type display devices are rather bulky and limited in the resolution that they provide.
Flat-panel display uses either a liquid crystal display (LCD) or gas-plasma technology. To form images, they use crystalline materials sandwiched between two panes of glass. When heat or voltage is applied, the crystals line up. This prevents light from passing through certain areas and produces the display. Gas-plasma displays, which provide better resolution but are more expensive than liquid crystal
displays, use gas trapped between glass to form images. The biggest advantage of flat-panel displays is that they are lightweight and compact.
(iii) File Manager and Query Manager File Manager is responsible for
(a) file structure,
(b) managing the space,
(c) locating block containing required record,
(d) requesting block from disk manager,
(e) transmitting required record to data manager.
Query Manager
(a) interprets user's online query,
(b) converts to an efficient series of operations,
(c) in a form is capable of being sent to data manager,
(d) uses data dictionary to find structure of relevant portion of database,
(e) uses information to modify query,
(f) prepares an optimal plan to access database for efficient data retrieval.
(iv) Candidate Key and Alternate Key
Candidate key is any set of one or more columns whose combined values are unique among all occurrences (i.e., tuples or rows). Since a null value is not guaranteed to be unique, no component of a candidate key is allowed to be null. In other words, we can say that a candidate key is a combination of attributes that can be uniquely used to identify a database record without any extraneous data. Each table may have one or more candidate keys.
Alternate key of any table is simply that candidate key(s) which is not currently selected as the primary key. An alternate key is a function of all candidate keys minus the primary key. In other words, we can say that if one table contains more than one candidate key, remaining candidate key column(s), which is not selected as a primary key is called Alternate Key.
DDL stands for Data Definition Language, which defines the conceptual schema providing a link between the logical (the way the user views the data) and physical (the way in which the data is stored physically) structures of the database. The logical structure of a database is a schema. A sub schema is the way a specific application views the data from the database. They define the physical characteristics of each record, fields in the record, field's data type, field's length, field's logical name and also specify relationships among the records. They describe the schema and subschema and indicate the keys of the record. They provide means for associating related records or fields, data security measures and for logical and physical data independence.
DML stands for Data Manipulation Language, which provides the data manipulation techniques like deletion, modification, insertion, replacement, retrieval, sorting and display of data or records and facilitate use of relationships between the records. They enable the user and application program to be independent of the physical data structures and database structures maintenance by allowing to process data on a logical and symbolic basis rather than on a physical location basis. They provide for independence of programming languages by supporting several high-level procedural languages
(vi) Online Backup and Offline Backup
Online Backup is performed on a database by executing the command-line or from the 'Backup Database' utility. When an online backup process begins, the database engine externalizes all cached data pages kept in memory to the database file(s) on disk. This process is called a checkpoint. The database engine continues recording activity in the transaction log file while the database is being backed up. The log file is backed up after the backup utility finishes backing up the database. The log file contains all of the transactions recorded since the last database backup. For this reason, the log file from an online full backup must be 'applied' to the database during recovery.
Offline Backup is performed on a database when the database is shutdown (offline). The log file from an offline backup does not have to participate in recovery but it may be used in recovery if a prior database backup is used.
(vii) Synchronous and Asynchronous Transmission
In Synchronous Transmission, bits are transmitted at fixed rate. The transmitter and receiver both use the same clock signals for synchronization. It allows characters to be sent down the line without start-stop bits and allows data to be send as a multi-word blocks. It uses a group of synchronization bits, which is placed, at the beginning and at the end of each block to maintain synchronization. The timing are determined by a MODEM. Here the transmission is faster because by removing the start and stop bits, many data words can be transmitted per second. The synchronous device is more expensive to build as it must be smart enough to differentiate between the actual data and the special synchronous characters.
In Asynchronous Transmission, each data word is accompanied by stop(1) and start (0) bits that identify the beginning and ending of the word. When no information is being transmitted (sender device is idle), the communication line is usually high (in binary 1), i.e., there is a continuous stream of 1. It is reliable as the start and stop bits ensure that the sender and receiver remain in step with one another. It is inefficient as the extra start and stop bits slow down the data transmission when there is a huge volume of information to be transmitted.
(viii) Analytical CRM and Collaborative CRM
In Analytical CRM, data gathered within operational CRM and/or other sources are analyzed to segment customers or to identify potential to enhance client relationship. Customer analysis typically can lead to targeted campaigns to increase share of customer's wallet. Data collection and analysis is viewed as a continuing and iterative process. Ideally, business decisions are refined over time, based on feedback from earlier analysis and decisions. Therefore, most successful analytical CRM projects take advantage of a data warehouse to provide suitable data. Business Intelligence is a related discipline offering some more functionality as separate application software.
Collaborative CRM facilitates interactions with customers through all channels like personal, letter, fax, phone, web, email and supports co-ordination of employee teams and channels. It is a solution that brings people, processes and data together so companies can better serve and retain their customers. The data/activities can be structured, unstructured, conversational, and/or transactional in nature. It enables efficient productive customer interactions across all communications channels and web collaboration to reduce customer service costs. It integrates call centers enabling multi-channel personal customer interaction and integrates view of the customer while interaction at the transaction level
SET stands for Secured Electronic Transaction, developed by a consortium led by MasterCard and Visa. SET is actually a combination of a protocol designed for use by other applications (such as Web browsers) and a standard (Recommended procedures) for handling credit card transactions over the Internet. Designed for cardholders, merchants, banks, and other card processors, SET uses digital certificates to ensure the identities of all parties involved in a purchase. SET also encrypts credit card and purchase information before transmission on the Internet.
JEPI stands for Joint Electronic Payment Initiatives, led by the World Wide Web Consortium and Commerce Net. JEPI is an attempt to standardize payment negotiations. On the buyer's side (the client side), it serves as an interface that enables a Web browser, and wallets, to use a variety of payment protocols. On the merchant's side (the serve side), it acts between the network and transport layers to pass off the incoming transactions to the proper transport protocol (for instance-email vs. HTTP,) and proper payment protocol (such as SET). Because it's likely that multiple protocols will be around for payment, transport, and wallets, JEPI makes it easier for the buyer to use a single application, and single interface, in a variety of commercial situations. It also makes it easier for the merchant to support the variety of payment system that customers will want to use.
(x) Strategic SCM and Operational SCM
Strategic SCM comprises of following activities:
(i) Strategic network optimization, including the number, location, and size of warehouses, distribution centers and facilities.
(ii) Strategic partnership with suppliers, distributors, and customers, creating communication channels for critical information and operational improvements such as cross docking, direct shipping, and third-party logistics.
(iii) Product design coordination, so that new and existing products can be optimally integrated into the supply chain.
(iv) Information Technology infrastructure, to support supply chain operations.
(v) Where to make and what to make or buy decisions.
Operational SCM comprises of following activities:
(i) Daily production and distribution planning, including all nodes in the supply chain.
(ii) Production scheduling for each manufacturing facility in the supply chain (minute by minute).
(iii) Demand planning and forecasting, coordinating the demand forecast of all customers and sharing the forecast with all suppliers.
(iv) Sourcing planning, including current inventory and forecast demand, in collaboration with all suppliers.
(v) Inbound operations, including transportation from suppliers and receiving inventory.
(vi) Production operations, including the consumption of materials and flow of finished goods.
(vii) Outbound operations, including all fulfilment activities and transportation to customers.
(viii) Order promising, accounting for all constraints in the supply chain, including all suppliers, manufacturing facilities, distribution centers, and other customers.
(ix) Performance tracking of all activities.
(xi) Program Design and Program Coding
In Program Design stage, the programmer develops the general organization of the program as it relates to the main functions to be performed. Out of several other tools available to him - input, output, file layouts and flowcharts are quite useful at this stage. These layouts, and flowcharts etc. are provided to the programmer by the system analyst. The flowchart depicts the flow of data, documents etc. very clearly, what are the steps to be repeated or what are the alternatives or branches at particular step. Such details may be difficult to bring out in descriptive language.
In Program Coding, the logic of the program outlined in the flowchart is converted into program statements or instructions at this stage. For each language, there are specific rules concerning format and syntax. Syntax means vocabulary, punctuation and grammatical rules available in the language manuals which the programmer has to follow strictly and pedantically.
5. (a) Computer systems as per their sizes are often categorized as follows:-
Super computers - Super computers are the largest and fastest computers available but are typically not used for commercial data processing. Instead they are used in specialized areas such as in defense, aircraft design and computer generated movies, weather research etc. Predicting the weather involves analyzing thousands of variables gathered by satellites, aircrafts and other meteorological stations on the ground. The first super computer was the ILLIAC IV made by Burroughs. Other suppliers of super computers are CRAY, CDC, Fujitsu, Intel Corporation, Thinking Machine Corporation, NEC, SGI, Hitachi, IBM and Sun Microsystems, etc.
Mainframe computers - Mainframes are less powerful and cheaper than Super computers. However, they are big general-purpose computers capable of handling all kinds of scientific and business applications. Mainframes can process several million instructions per second and can support more than 1,000 remote terminals. These have large on-line secondary storage capacity. A number of different types of peripheral devices like magnetic tape drive, hard disk drive, visual display units, plotters, printers and telecommunication terminals can be attached with main-frame computers. They have high-speed cache memory which enables them to process applications at a faster rate than mini or microcomputers. They also offer the facility of multiprogramming and time-sharing.
Minicomputers - These type of computers perform data processing activities in the same way as the mainframe but on a smaller scale at lower cost. Data is usually input by means of a keyboard. As the name implies, a minicomputer is small compared with a mainframe and may be called a scaled-down mainframe as the processor and the peripherals are physically smaller. A minicomputer system consists of a CPU, several disk drives, a high-speed printer, perhaps a few magnetic tape units, and number of terminals.
Microcomputers - Microcomputers are a full-fledged computer systems that use a microprocessor as its CPU, and are also called as Personal Computer Systems. Microcomputers were first available for widespread use in the 1970s, when it became possible to put the entire circuitry of computers (CPU) onto a small silicon chip called microprocessor. A microprocessor is a product of the microminiaturization of electronic circuitry; it is literally a "computer on a chip. Chip refers to any self-contained integrated circuit.
(b) Workstations Versus Minicomputers
Workstations differ significantly from microcomputer in two areas. Internally, workstations are constructed differently than microcomputers. They are based on different architecture of CPU called Reduced Instruction Set Computing (RISC), which results in faster processing of instructions.
The other difference between workstations and microcomputers is that most microcomputers can run any of the four major operating systems - DOS, Unix, OS/2, and Microsoft Windows NT, but workstations generally run the Unix operating systems or a variation of it. The biggest manufacturer of workstations is Sun Microsystems. Other manufacturers include IBM, DEC, Hewlette Packard and Silicon Graphics.
Many people use the term workstation to refer to any computer or terminal that is connected to another computer. Although this was once a common meaning of the term, it has become outdated. These days, a workstation is powerful RISC - based computer that runs the Unix Operating System and is generally used by scientists and engineers.
6. (a) Central Processing Unit: The Central Processing Unit (CPU) also known as the processor is the heart, soul and brain of the computer. In a microcomputer, an entire CPU is contained on a tiny chip called a microprocessor. It is the most important component on the system's motherboard. The processor computes and processes data and delivers the results based on the instructions that are fed to the PC. Every CPU has at least two basic parts - the Control Unit and the Arithmetic Logic Unit.
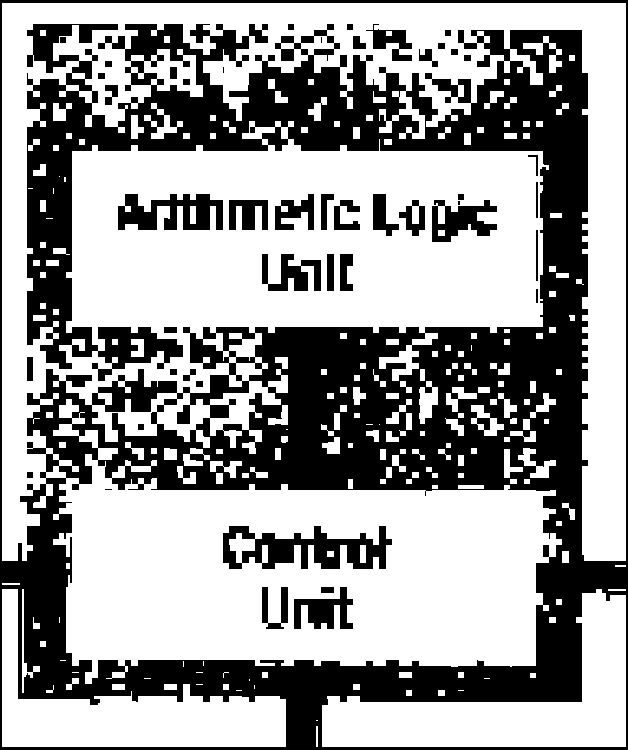 |
|
CPU (Central Processing Unit) |
The Control Unit
All the computer's resources are managed from the control unit. The control unit can be considered as a traffic cop directing the flow of data. It is the logical hub of the computer. The CPU's instructions for carrying out commands are built into the control unit.
The Arithmetic Logic Unit
Because computers store all the data as numbers, a lot of the processing that takes place involves comparing numbers or carrying out mathematical operations. In addition to establishing ordered sequences and changing those sequences, the computer can perform only two types of operations: arithmetic operations and logical operations. Arithmetic operations include addition, subtraction, multiplication, and division. Logical operations include comparisons, such as determining whether one number is equal to, greater than, or less than another number.
(b) Various features of the Central Processing Unit : The various features that the Central Processing Unit of a PC offers are as follows:-
Clock Speed: The clock speed is the speed at which the processor executes instructions. Clock speed is measured in megahertz (MHz) which is a million cycles per second. Therefore, a 450 MHz processor performs 450 million instructions per second. Higher the clock's speed, the faster the processor, the better the system performance. Also, some microprocessors are super scalar, which means that they can execute more than one instruction per clock cycle.
Cache: Processors incorporate their own internal cache memory. The cache acts as temporary memory and boosts processing power significantly. The cache that comes with the processor is called Level One (L1) cache. This cache runs at the processor's clock speeds, and therefore is very fast. The L1 cache is divided into 2 sections, one for data, and the other for instructions. Generally, more the L1 cache, faster the processor. Additionally, PCs also include a much slower secondary, or Level Two (L2) cache. This cache resides on the motherboard and delivers slower performance when compared with the L1 cache. To overcome this limitation, newer chips (Pentium II and Pentium III) house the L2 cache in a cartridge along with the CPU.
Architecture: The CPUs architecture determines the manner in which it processes data. New CPUs employ multi-staged pipelines for transmitting data. To ensure proper data flow through these lines, the CPU includes a kind of prediction and error correction mechanism.
Slot: Different processors use different sockets or slots to fit onto the motherboard. Based on the type of processors, there are two main types of slots for connecting to the motherboard, Socket 7 and Slot 1. Socket 7 is a 321-pin socket for Pentium class CPUs, Pentium MMX, K5, and K6, ranging from 75 MHz to 200 MHz processors. However, the Pentium II/III CPUs use Slot 1 for connecting to the motherboard. Instead of the usual manner in which a CPU fits onto the motherboard, Slot 1 CPUs fit onto the motherboard as a daughter card, allowing for faster communication between the CPU and the L2 cache.
Density: A CPU is made up of millions of small transistors and performs all the calculation and manipulation operations by synchronizing between the transistors. Therefore, the shorter the distance between two transistors on a CPU, the faster the performance. Older CPUs had a distance of one micron between the transistors. But, newer CPUs have a distance as small as 0.35 micron between two transistors, delivering faster performance.
MMX: MMX stands for Multimedia Extensions, which is a set of instructions built in to the CPU, specifically intended for improving the performance of multimedia or graphic applications, mainly games. However, one needs to have applications specifically designed to take advantage of MMX.
7. (a) Direct Data Entry devices refer to the entry of data directly into the computers through machine readable source documents. DDE does not require manual transcription of data from original paper documents. DDE devices can scan source documents magnetically or optically to capture data for direct entry into the computer. Some of the direct data entry devices are as follows:-
Magnetic Ink Character Recognition (MICR): MICR employs a system of printed characters which are easily decipherable by human beings as well as a machine
reader. It uses special printing font to represent characters. In this font, each character is basically composed of vertical bars. The characters are printed in special ink, which contain a magnetizable material. This method is primarily used in banking industry, and most cheques are now processed under the MICR approach.
Optical Character Reader (OCR): OCR also employs a set of printing characters with standard font that can be read by both human and machine readers. The machine reading is done by light scanning techniques in which each character is illuminated by a light source and the reflected image of the character is analyzed in terms of the light-dark pattern produced. Keyboard devices are used to give the required print quality. OCR has the potential of reading even handwritten documents straightway, can read upper and lower case letters, numerics and certain special characters from handwritten, typed and printed paper documents. The specific characters that can be read and whether the characters must be handwritten, typed or printed depend upon the type of OCR being used.
Optical Mark Recognition (OMR): Optical marks are commonly used for scoring tests. OMR can also be used for such applications as order writing, payroll, inventory control, insurance, questionnaires, etc. However, it is to be noted that designing the documents for OMR is rather a tough task. They should be simple to understand otherwise errors may result more perhaps than would occur in using traditional source documents and keypunching from them.
Smart Card System: Smart card resembles credit cards in size and shape; however, it contains a microprocessor chip and memory, and some include a keypad as well. These were pioneered in France and many organizations are still just experimenting with them. In many instances, smart cards make it possible for organizations to provide new or enhanced services for customers. So far, smart cards are used most frequently to make electronic purchases and to electronically transfer funds between accounts. However, the potential applications for these are abound.
Bar Code Reader: The most widely used input device after the keyboard and mouse is the flatbed or hand-held bar code reader commonly found in supermarkets and departmental stores. These devices convert the bar code, which is a pattern of printed bars on products, into a product number by emitting a beam of light -frequently a laser beam which reflects off the bar code image. A light-sensitive detector identifies the bar code image by recognizing special bars at both ends of the image. Once the detector has identified the bar code, it converts the individual bar patterns into numeric digits. After the bar code reader has converted a bar code image into a number, it feeds that number to the computer, just as though the number had been typed on a keyboard.
Image Processing: Image Processing captures an electronic image of data so that it can be stored and shared. Imaging systems can capture almost anything, including keystroke or handwritten documents (such as invoices or tax returns), flowcharts, drawings, and photographs. Many companies that use document imaging are making significant progress toward paperless offices. There are five distinct steps to document imaging - data capture, indexing, storage, retrieval, and output.
(b) The advantages of Image Processing are as follows:-
(i) Accessibility : Documents can be accessed and reviewed simultaneously by many people, even from remote locations.
(ii) Accuracy: Accuracy is much higher because costly and error-prone manual data-entry processes are eliminated.
(iii) Availability: There are no more lost or misfiled documents.
(iv) Capacity: Vast amounts of data can be stored in very little space, which significantly reduces storage and office space.
(v) Cost : When large volumes of data are stored and processed, the cost per document is quite inexpensive. As a result, the costs to input, file, retrieve, and refile documents are reduced significantly.
(vi) Customer satisfaction : When waiting time is significantly reduced (due to lost or misfiled documents, queue time, etc.), customers can get the information almost immediately.
(vii) Security : Various levels of passwords (network, data base, files, etc.) and clearances can be assigned to restrict document access.
(viii) Speed : Data can be retrieved at fantastic speeds. Stored documents can be indexed using any number of identifying labels, attributes, or keywords.
(ix) Versatility: Handwritten or typed text can be added to an image, as can voice messages. Documents can be added to word processing files; the data can be included in a spreadsheet or data base.
8. The programming languages are part of the software or programming aids provided by the manufacturer. A programming language is a language used in writing programs to direct processing steps to be carried out by a computer. A wide variety of computer programming languages are available. The programmer must be familiar with one or more of them in order to write a computer program. Each programming language has very specific standards and rules of use, which the programmer must know and adhere to when developing a program. The programming languages can be divided as follows:-
Machine Language or First Generation Languages : In the early days of computer, all programs were written in machine codes. Each particular computer model has a machine language, which is based on the internal engineering architecture of the equipment, and which is developed and provided to user by the computer manufacturer.
Assembler Languages or Second Generation Languages : Assembler Languages are at the next level in improvement over the machine languages. They are also known as symbolic languages because they employ symbols for both arithmetic and logical operations and even location addresses. Since mnemonic symbols are being used, this eases up the programmer's task greatly. But the computer follows its machine language only and the program written in the assembler language has to be translated. This is accomplished by a special program usually supplied by the computer manufacturer and known as the Assembler.
Compiler Languages (High-level-languages) or Third Generation Languages :
Compiler languages are also known as High Level Languages or Procedural Languages. They are procedure oriented (viz., a business application oriented language COBOL and a scientific application oriented language FORTRAN. They employ plain English like and mathematical expressions. They are detached from the machine design and therefore the nomenclature High level' Languages. Since they are procedure oriented and detached from the machine design, instructions of these languages may be equivalent to more than one instructions in a machine language. An instruction in these languages is usually called a statement.
The Fourth Generation Languages (4GLs) : The trend in software development is toward using high level user friendly Fourth Generation Languages (4 GLs) There are two types of 4GLs :
(i) Production Oriented 4GLs - Production-Oriented 4GLs are designed primarily for computer professionals. They use 4GLs such as ADR's, Ideal, Software AG's Natural 2, and Cincoms Mantis to create information systems. Professional programmers who use 4GLs claim productivity improvements over Third Generation procedure oriented languages such as (COBOL, FORTRAN, BASIC and so on) of 200% to 1000%.
(ii) User Oriented 4GLs - This type of 4GLs is designed primarily for end users. Users write 4GL programs to query (extract information from) a database and to create personal or departmental information systems. User-oriented 4GLs include Mathematical Products Group's RAMIS-II and Information Builders' FOCUS.
Object-Oriented Languages and Programming: Using object-oriented programming (OOP), objects are combined and the small amount of code necessary for finishing the program is written. Rather than writing a program line by line, programmers select objects by pointing to a representative icon and then linking these objects together. Objects can be modified, reused, copied, or created. When an object is updated, all programs using that object can be automatically updated as well. These objects are then sent messages telling them what to do; the objects complete the task accordingly. For
example, selecting an object that looks like a fax machine would mean that data are to be sent by fax. This programmer-machine interface is more natural, powerful, and easy to understand and use than more traditional methods.
9. (a) Following are some of the purposes of application software:-
(i) To provide multiple applications, which can be bundled together as a package. The separate application in a suite usually have a user interface that has some commonality making it easier for the user to learn and use each application. And often they may have some capability to interact with each other in ways beneficial to the user
(ii) It provides a user-written software that tailors systems to meet the user's specific needs. User-written software includes spreadsheet templates, word processor macros, scientific simulations, graphics and animation scripts. Even email filters are a kind of user software. Users create this software themselves and often overlook how important it is.
(iii) It provides a platform where a particular application or problem is solved. Examples of such programs are payroll, general accounting, sales statistics and inventory control etc. Usually different organizations require different programs for similar application and hence it is difficult to write standardized programs. However, tailor-made application software can be written by software houses on modular design to cater to the needs of different users.
(b) Enterprise Resource Planning systems (ERPs) integrate (or attempt to integrate) all data and processes of an organization into a single unified system. A typical ERP system uses multiple components of computer software and hardware to achieve the integration. A key ingredient of most ERP systems is the use of a single, unified database to store data for the various system modules.
The term ERP originally implied systems designed to plan the utilization of enterprise-wide resources. ERP systems typically attempt to cover all basic functions of an organization, regardless of the organization's business or charter. Business, non-profit organizations, governments, and other large entities utilize ERP systems. Additionally, in order to be considered an ERP system, a software package generally would only need to provide functionality in a single package that would normally be covered by two or more systems. Technically, a software package that provides both Payroll and Accounting functions (such as QuickBooks) would be considered an ERP software package.
The introduction of an ERP system to replace two or more independent applications eliminates the need for interfaces previously required between systems, and provides additional benefits that range from standardization and lower maintenance (one system instead of two or more) to easier and/or greater reporting capabilities (as all data is typically kept in one database). Examples of modules in an ERP which formerly would have been stand-alone applications include: Manufacturing, Supply Chain, Financials, CRM, Human Resources, and Warehouse Management.
10. Following are the examples of DSS (Decision Support Systems) in accounting:
Cost Accounting System: The health care industry is well known for its cost complexity. Managing costs in this industry require controlling costs of supplies, expensive machinery, technology, and a variety of personnel. Cost accounting applications help health care organizations calculate product costs for individual procedures or services. Decision support systems can accumulate these product costs to calculate total costs per patient. Health care managers may combine cost accounting decision support systems with other applications, such as productivity systems. Combining these applications allows managers to measure the effectiveness of specific operating processes. One health care organization, for example, combines a variety of DSS applications in productivity, cost accounting, case mix, and nursing staff scheduling to improve its management decision making.
Capital Budgeting System: Companies require new tools to evaluate high-technology investment decisions. Decision makers need to supplement analytical techniques, such as net present value and internal rate of return, with decision support tools that consider some benefits of new technology not captured in strict financial analysis. One decision support system designed to support decisions about investments in automated manufacturing technology is AutoMan, which allows decision makers to consider financial, nonfinancial, quantitative, and qualitative factors in their decision-making processes. Using this decision support system, accountants, managers, and engineers identify and prioritize these factors. They can then evaluate up to seven investment alternatives at once.
Budget Variance Analysis System: Financial institutions rely heavily on their budgeting systems for controlling costs and evaluating managerial performance. One institution uses a computerized DSS to generate monthly variance reports for division comptrollers. The system allows these comptrollers to graph, view, analyse, and annotate budget variances, as well as create additional one-and five-year budget projections using the forecasting tools provided in the system. The decision support system thus helps the controllers create and control budgets for the cost-center managers reporting to them.
General Decision Support System; As mentioned earlier, some planning languages used in DSS are general purpose and therefore have the ability to analyze many different types of problems. In a sense, these types of decision support systems are a decision maker's tools. The user needs to input data and answer questions about a specific problem domain to make use of this type of decision support system.
Expert Choice: This program supports a variety of problems requiring decisions. The user works interactively with the computer to develop a hierarchical model of the decision problem. The decision support system then asks the user to compare decision variables with each other. For instance, the system might ask the user how important cash inflows are versus initial investment amount to a capital budgeting decision. The decision maker also makes judgments about which investment is best with respect to these cash flows and which requires the smallest initial investment. Expert Choice analyzes these judgments and presents the decision maker with the best alternative.
11. (a) Expert systems can be example-based, rule based, or frame based.
Using an example-based system, developers enter the case facts and results. Through induction the ES converts the examples to a decision tree that is used to match the case at hand with those previously entered in the knowledge base.
Rule-based systems are created by storing data and decision rules as if- then -else rules. The system asks the user questions and applies the if-then-else rules to the answers to draw conclusions and make recommendations. Rule -based systems are appropriate when a history of cases is unavailable or when a body of knowledge can be structured within a set of general rules.
Frame-based systems organize all the information (data, descriptions, rules etc.) about a topic into logical units called frames, which are similar to linked records in data files. Rules are then established about how to assemble or inter-elate the frames to meet the user's needs.
Expert systems provide several levels of expertise. Some function as assistants that perform routine analysis and call the user's attention to tasks that require human expertise. Others function as colleagues, and the user "discusses a problem with the system until both agree on a solution. When a user can accept the system's solution without question, the expert system can be referred to as a true expert. Developers of expert systems are still striving to create a true expert; most current systems function at the assistant or colleague level.
(b) Expert systems offer the following benefits:
1. They provide a cost-effective alternative to human experts.
2. They can outperform a single expert because their knowledge is representative of numerous experts. They are faster and more consistent and do not get distracted, overworked, or stressed out.
3. They produce better-quality and more consistent decisions. Expert systems assist users in identifying potential decision making problems, which increases the probability that sound decisions will be made.
4. They can increase productivity.
5. They preserve the expertise of an expert leaving the organization.
6. Although expert systems have many advantages and great promise, they also have a significant number of limitations.
7. Development can be costly and time-consuming. Some large systems required up-to 15 years and millions of dollars to develop.
8. It can be difficult to obtain knowledge from experts who have difficulty specifying exactly how they make decisions.
9. Designers have not been able to program what humans consider common sense into current systems. Consequently, rule-based systems break down when presented with situations they are not programmed to handle.
10. Until recently, developers encountered skepticism from businesses due to the poor quality of the early expert systems and the high expectations of users.
12. (a) Following are the management problems of file processing:
1. Data Duplication: Independent data files include a lot of duplicated data; the same data (such as a customer's name and address) is recorded and stored in several files. This data redundancy causes problems when data has to be updated, since separate file maintenance programs have to be developed and coordinated to ensure that each file is properly updated. Of course, this proves difficult in practice, so a lot of inconsistency occurs among data stored in separate files.
2. Lack of Data Integration: Having data in independent files makes it difficult to provide end users with information for ad hoc requests that require accessing data stored in several different files. Special computer programs have to be written to retrieve data from each independent file. This is difficult, time consuming, and expensive for the organizations.
3. Data Dependence: In file processing systems, major components of a system
i.e., the organization of files, their physical locations on storage, hardware and the application software used to access those files depend on one another in significant ways. For example, application programs typically contain references to the specific format of the data stored in the various files they use. Thus, if changes are made in the format and structure of data and records in a file, changes have to be made in all the programs that use this file. This program maintenance effort is a major burden of file processing systems. It is difficult to do it properly, and it results in a lot of inconsistency in the data files.
4. Other Problems: In file processing systems, data elements such as stock numbers and customer addresses are generally defined differently by different end users and applications. This causes serious inconsistency in the development of programs which access such data. In addition, the integrity (i.e. the accuracy and completeness) of the data is suspected because there is no control over their use and maintenance by authorized end users.
(i) Naive users, who are not aware of the presence of the database system supporting the usage,
(ii) Online users, who may communicate with database either directly through online terminal or indirectly through user interface or application programs. Usually they acquire at least some skill and experience in communicating with the database,
(iii) Application programmers, who are responsible for developing the application programs and user interfaces,
(iv) Database Administrator, who can execute centralized control and is responsible for maintaining the database. He is most familiar with the database.
13. Developing a backup and recovery strategy: The steps suggested in the development of a backup and recovery strategy consist of the following:
> Understand what backup and recovery means to the business;
> Management commits time and resources for the project;
> Develop, test, time, document, health check, deploy, and monitor;
> Beware of any external factors that affect recovery;
> Address secondary backup issues.
(i) Understand what backup and recovery means to the business: If the recovery time is in minutes, then database backup and recovery is critical to the business needs and it is paramount that the user implement some kind of backup and recovery strategy. If recovery can take hours, then the user has more time to perform the tasks. If recovery can be expressed in terms of days then the urgency to recover the database still exists, but time appears to be less of a factor.
(ii) Management commits time and resources for the project: Management must decide to commit financial resources towards the development and implementation of a backup and recovery strategy. The strategy can be basic or quite extensive depending upon the business needs of the company. After developing a backup and recovery strategy, management should be informed of the expected backup and recovery times. and alternative solutions must be prepared countering the timings of anticipated issues. These alternative solutions could be requesting additional hardware, improved backup medium, altering backup schedule, accepting a longer recovery time versus backup time. Then it will be up to management to decide what solution fits their corporate needs.
(iii) Develop, test, time, document, health check, deploy, and monitor : These
phases are the core in developing a backup and recovery strategy:
Create backup and recovery commands. Verify these commands work as designed. Does the full or incremental online backup work? Verify that the commands product the desired results.
Time estimates from executing backup and recovery commands help to get a feel for how long will these tasks take. Use this information to identify what commands will be executed and when.
Document the backup commands and create written procedures outlining where the backups are kept and identify the naming convention used as well as the kind of backups performed. This information can be very important when an individual must check the backups or perform a database recovery and the data base administrator (DBA) is not available.
Incorporate health checks into the backup procedures. We should check the database to ensure the database is not corrupt. One can perform a database health check prior to backing up a database or on a copy of the database from the backup.
Deployment of the backup and recovery consists of setting up the backup procedures on the production server. Verify the necessary hardware is in place and any other supporting software necessary to perform these tasks. Modify procedures to reflect the change in environment. Change user id, password, server and database name to reflect the change in environment.
Monitor backup procedures to avoid unexpected errors. Make sure any changes in the process are reflected in the documentation.
(iv) Beware of external factors that affect recovery: External factors that effect database recovery are time, hardware, and software. Allow additional recovery time for entering miscellaneous tasks that must be performed. Factors that influence time are the size of database files, recovery medium, disk space, and unexpected errors. The addition of more files into the recovery scenario, increases the places where recovery can fail. As the backup and recovery strategy develops, it may be necessary to check the performance of the equipment and software ensuring it meets the expectations.
(v) Protect database backups by performing health checks: Database health checks are run against the database and log files to ensure they are not corrupt. The database validity utility is used to scan every record in every table and looks up each record in each index on the table. If the database file is corrupt, the user needs its recovery from the previous database backup. A
database can be validated before being backed up or against a copy of the database from the backup.
14. (a) Different methods of storing data in a data warehouse : All data warehouses store their data grouped together by subject areas that reflect the general usage of the data (Customer, Product, Finance etc.). The general principle used in the majority of data warehouses is that data is stored at its most elemental level for use in reporting and information analysis. Within this generic intent, there are two primary approaches to organizing the data in a data warehouse.
The first is using a "dimensional" approach. In this style, information is stored as "facts" which are numeric or text data that capture specific data about a single transaction or event, and "dimensions" which contain reference information that allows each transaction or event to be classified in various ways. As an example, a sales transaction would be broken up into facts such as the number of products ordered, and the price paid, and dimensions such as date, customer, product, geographical location and sales person. The main advantage of a dimensional approach is that the Data Warehouse is easy for business staff with limited information technology experience to understand and use. Also, because the data is pre-processed into the dimensional form, the Data Warehouse tends to operate very quickly. The main disadvantage of the dimensional approach is that it is quite difficult to add or change later if the company changes the way in which it does business.
The second approach uses database normalization. In this style, the data in the data warehouse is stored in third normal form. The main advantage of this approach is that it is quite straightforward to add new information into the database, whilst the primary disadvantage of this approach is that it can be quite slow to produce information and reports.
(b) Concerns in using data warehouse
(i) Extracting, cleaning and loading data could be time consuming.
(ii) Data warehousing project scope might increase.
(iii) Problems with compatibility with systems already in place e.g. transaction processing system.
(iv) Providing training to end-users, who end up not using the data warehouse.
(v) Security could develop into a serious issue, especially if the data warehouse is web accessible.
(vi) A data warehouse is a high maintenance system.
(i) Organizations can improve communication by connecting their computers and working on standardized systems, so that:
Staff, suppliers and customers are able to share information and get in touch more easily;
More information sharing can make the business more efficient - e.g. networked access to a common database can avoid the same data being keyed multiple times, which would waste time and could result in errors;
staff equipped to deal with queries,deliver a better standard of service as they can share information about customers.
(ii) Organization can reduce costs and improve efficiency - by storing information in one centralized database and streamlining working practices, so that:
staff can deal with more customers at the same time by accessing customer and product databases;
network administration can be centralized, less IT support is required;
costs are cut through sharing of peripherals such as printers, scanners, external discs, tape drives and Internet access.
(iii) Organizations can reduce errors and improve consistency - by having all staff work from a single source of information, so that standard versions of manuals and directories can be made available, and data can be backed up from a single point on a scheduled basis, ensuring consistency.
(b) Following are the various data transmission techniques:-
(i) Circuit Switching: Circuit switching is what most of us encounter on our home phones. We place a call and either get our destination party or encounter a busy signal incase of which we can not transmit any message. A single circuit is used for the duration of the call.
(ii) Message Switching: Some organizations with a heavy volume of data to transmit use a special computer for the purpose of data message switching. The computer receives all transmitted data; stores it; and, when an outgoing communication line is available, forwards it to the receiving point.
(iii) Packet Switching: It is a sophisticated means of maximizing transmission capacity of networks. This is accomplished by breaking a message into transmission units, called packets, and routing them individually through the network depending on the availability of a channel for each packet. Passwords and all types of data can be included within the packet and the transmission
cost is by packet and not by message, routes or distance. Sophisticated error and flow control procedures are applied on each link by the network.
16. (a) Business uses of Internet: The Internet is a pathway to various sites that contain information. In today's age no one is able to conduct any worthwhile business unless the business communication occurs on e-mail. An e-mail address is the basic facility that anyone on the Internet gains. The communication is quicker and more convenient that any other mode ever used. It is reliable and provides easy identification of sender. Electronic mail works similar to paper mail through postal system but is entirely electronic through the Internet, users can have online interactive communication. This is another major facilitator for any business. Most businesses need a lot of interaction internally among their executives and externally with business associates, when many persons have to contribute to discussions. This is normally achieved by arranging meetings and conferences for which people travel from different locations to come together at one place. This "many to many communications can be handled on the Internet quite effectively, without any need for people to travel. At pre-defined timings, those who have to communicate together can be online through Internet and have electronic conferences. Similarly, many discussions can be done through a forum where people post messages for each other and respond to them periodically. Businesses require a lot of external information in various functions regularly for taking decisions. For this, lot of time is spent in searching and getting information. Internet is a storehouse of information and is able to cater to a very wide range of information needs. This is possible since users are able to electronically identify common interest groups and share information. It is easy to create databases and make information accessible to other users on the Internet. Users have to only search for information sites, qualify and retrieve useful information.
When business need to make information on their products and services available to others, e.g. for their clients, Internet provides a very convenient vehicle. Such businesses can set up their own web sites or home pages. When the potential clients and others visit the site or the "home pages, they will have the option to send
(b) Electronic Commerce impacts a broad number of business activities such as:
marketing, sales and sales promotion;
pre-sales, subcontracts, supply;
financing and insurance;
commercial transactions: ordering, delivery, payment;
product service and maintenance;
co-operative product development;
distributed co-operative working;
use of public and private services;
business-to-administrations (concessions, permissions, tax, customs, etc);
transport and logistics;
public procurement;
automatic trading of digital goods;
accounting.
17. (a) To be effective, the CRM (Customer Relationship Management) process needs to
be integrated end-to-end across marketing, sales, and customer service. A good CRM program needs to:
(i) Identify customer success factors;
(ii) Create a customer-based culture;
(iii) Adopt customer-based measures;
(iv) Develop an end-to-end process to serve customers;
(v) Recommend what questions to ask to help a customer solve a problem;
(vi) Recommend what to tell a customer with a complaint about a purchase;
(vii) Track all aspects of selling to customers and prospects as well as customer support.
(b) A CRM solution is characterized by the following functionality:
Scalability - the ability to be used on a large scale, and to be reliably expanded to whatever scale is necessary.
Multiple communication channels - the ability to interface with users via many different devices (phone, WAP, internet, etc)
Workflow - the ability to trigger a process in the back office system, e. g. Email Response, etc.
Assignment - the ability to assign requests (Service Requests, Sales Opportunities) to a person or group.
Database - the centralized storage (in a data warehouse) of all information relevant to customer interaction
Customer privacy considerations - the data encryption and the destruction of records are needed to ensure that they are not stolen or abused.
18. (a) A number of additional concerns about initiating electronic commerce on the
Internet must be addressed before these businesses are ready to take the "electronic plunge:
Reliability: Will the service level that the company depends upon to conduct business always be available? America Online customers, for example, experienced a 19-hour outage in August of 1996.
Scalability: How can the Internet and individual services be scaled to meet the needs and expectations of all businesses?
Ease of use: Can methods be developed to promote easy access and use to all potential trading partners? Will small businesses be at a disadvantage due to a lack of technical sophistication and resources?
Payment methods: What will be an appropriate, safe, and reliable payment method for electronic commerce?
Many other concerns about the vulnerability of the Internet include the risks inherent in electronic mail transactions, the threat of computer viruses, and the existence of unprofessional employees. Companies or consumers passing information through email that can be intercepted bringing risk to both parties. Businesses connected to the Internet that also store important company information in the same location are subject to tampering, and their information may be accessed and possibly damaged. Financial information such as credit card numbers may be stolen and used by unauthorized parties to make illegal purchases, resulting in damage to customers and businesses alike. These fraudulent purchases, unfortunately, are charged to the customer and prove difficult for the businesses to collect.
(b) Encryption allows information to transit the Internet while being protected from interception by eavesdroppers. There are two basic approaches to encryption:
(i) Hardware encryption devices are available at a reasonable cost, and can support high - speed traffic. If the Internet is being used to exchange information among branch offices or development collaborators, for instance, use of such devices can ensure that all traffic between these offices is secure.
(ii) Software encryption is typically employed in conjunction with specific applications. Certain electronic mail packages, for example, provide encryption and decryption for message security.
 |
|
CLEAR ALL WORKING LOCATIONS |
READ J (1)
J (2)... J (2500)
|
\ Ns | ||||
|
y/ LAST X |
l=l +1 | |||
|
p2 = p2 + 1 |
'RECRD/ |
|
R1 |
= P1/2500 |
|
* | |
|
*2 |
= P2/2500 |
|
* | |
|
*3 |
= P3/25OO |
|
v | |
|
R4 |
= P4/2500 |
PRINT R1
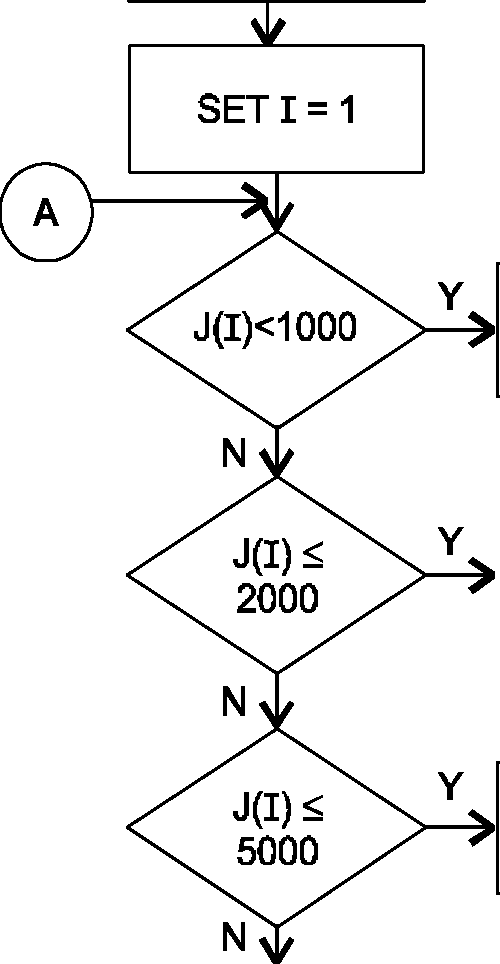 |
P1=P1+1 P3 = P3 + 1 |
|
P4=P4 + 1 | |
STOP
R4
|
Rules | ||||||||
|
Hire Purchase Scheme : Conditions |
R1 |
R2 |
R3 |
R4 |
R5 |
R6 |
R7 | |
|
C1. |
Customer holds the present job for more than 5 years |
Y |
Y |
Y |
Y |
N |
N |
N |
|
C2. |
Resides in the same place at least for 3 years |
Y |
Y |
N |
N |
Y |
N |
N |
|
C3. |
Monthly salary of the customer exceeds Rs. 2000 |
Y |
N |
Y |
N |
Y |
N |
- |
|
Actions | ||||||||
|
A1. |
Give credit upto Rs. 3000 |
X | ||||||
|
A2. |
Give credit upto Rs. 4000 |
X |
X | |||||
|
A3. |
Give credit upto Rs. 5000 |
X | ||||||
|
A4. |
Reject credit |
X |
X |
X | ||||
101
|
Attachment: |
| Earning: Approval pending. |
