The Institute of Chartered Financial Analysts of India University 2010 C.A Chartered Accountant Professional Edution II (PE-II) Revision Test s- 6- Information Technology - Question Paper
May 2010: The Institute of Chartered Accountants of India - Revision Test ques. papers (RTPs) Professional Education II Course (PE-II) Examination: Paper 6- info Technology: May 2010 University ques. paper
PAPER - 6 : INFORMATION TECHNOLOGY
QUESTIONS
1 Define the following term briefly.
|
(i) |
Toggle |
(ii) |
Data item |
(iii) |
EBCDIC System |
|
(iv) |
Accumulator |
(v) |
CMOS |
(vi) |
Cursor |
|
(vii) |
PCI Slots |
(viii) Intelligent Terminal |
(ix) |
Drag | |
|
(x) |
Duplex Printing |
(xi) |
Overlay |
(xii) |
Seek Time |
|
(xiii) Object Program |
(xiv) Debug |
(xv) |
Interpreter | ||
(xvi) SQL (xvii)Client (xviii) Multiplexer
(xix) Bridge (xx) FTP (xxi) URL
(xxii)PPP (xxiii) ISP (xxiv)Asymmetric Crypto System
2. Convert the following from one number system to another number system along with the working notes:
|
(i) |
(324.25)10 = ( |
)2 | |
|
(ii) |
(11101101.0101)2 = ( |
)10 | |
|
(iii) |
= CO 3) 4 4 CO |
)16 | |
|
(iv) |
(568.5)10 = ( |
)8 | |
|
(v) |
(292A)16 = ( |
)10 | |
|
(vi) |
(10110101.11)2 = ( |
)8 | |
|
(vii) |
(6DAF)16 = ( |
)2 | |
|
(viii) |
= 2 01 01 01 01 0 |
)16 | |
|
(ix) |
(CD.1C)16 = ( |
)8 | |
|
(x) |
(310.04)8 = ( |
)2 | |
|
Give |
one or two uses or reasons of each |
of the following: | |
|
(i) |
Use of Master File |
(ii) Use of Data Bus | |
|
(iii) |
Use of Parallel port |
(iv) Use of Integrated Circuits | |
|
(v) |
Use of Disk Formatting |
(vi) Use of Spooling S/W | |
|
(vii) |
Use of Modem |
(viii) Use of Hub | |
|
(ix) |
Use of Firewall |
(x) Use of Intranet | |
|
(xi) |
Use of Auxiliary Storage Devices |
(xii) Use of Boot Strap loader | |
|
(xiii) |
Use of Language Translators |
(xiv) Use of Repeaters | |
|
(xv) |
Use of Router | ||
4. Distinguish between the following:
(i) Thing Generation and Fourth Generation Language
(ii) Dynamic RAM and Static RAM
(iii) Control Unit and Arithmetic Logic Unit
(iv) Personal computing and Networking Computing
(v) Impact Printer and Non-impact Printer
(vi) CD-ROM and ROM BIOS
(vii) Multiprogramming and Multitasking systems
(viii) Systems software and Application software
(ix) Sequential File Organization and Random File Organization
(x) Online System and Real time system
(xi) Local area network and Wide Area network
(xii) Client-server Architecture and Peer-to-peer Architecture
(xiii) Network Attached Storage and Direct Attached Storage
(xiv) Audio Conferencing and Video Conferencing
(xv) Horizontal Partitioning and Vertical Partitioning Data Processing
5. (a) Discuss various types of computer systems in brief.
(b) What do you understand by computer? Discuss Advantages and Limitations of computer system.
Anatomy of Computer
6. (a) Discuss various features of central processing unit in brief.
(b) What do you understand by system memory? Discuss in brief various types of system memory.
Computer Input Media and Devices
7. (a) Discuss various data entry devices used for transcribing source information on
magnetic media.
(b) What is screen resolution? Discuss various display adapters used in personal computer.
Computer Output
8. (a) Discuss the main features of Chain printer and Drum printer.
(b) Discuss various non-impact printers viz. Thermal, Inkjet and Laser printer in brief.
9. (a) What are the factors that determine the number of charters that can be stored in a
floppy diskette?
(b) Discuss various types of Optical Laser Disks in brief.
Software
10. (a) What are the various Files and Directories used in Opening System. Discuss in
brief.
(b) What is Language Translators? Discuss various types of Languages Translators in brief.
Data Storage and Retrieval
11. (a) What are the factors that determine the best file organization for an application?
(b) What do you understand by Data Access and Organization Methods? Discuss Sequential method in brief.
Database Management Systems
12. (a) What are the management problems of files processing system?
(b) Briefly describe various components of the database environment.
Advance Systems
13. (a) What is Decision Support System? Briefly discuss various characteristics of a
Decision Support System.
(b) What do you understand by Artificial Intelligence? Describe various types of Artificial Intelligence.
Telecommunication and Networking
14. (a) What do you understand by Network Topology? Describe Various Network topology
in brief.
(b) Discuss in brief various components of a Local Area Network.
Internet and Emerging Technologies
15. (a) Describe the term Internet. What benefits are offered by the Internet?
(b) What is E-commence? Describe three general classes of E-commerce in brief. Database Performance Monitoring
16. (a) What are the five areas of DBMS that should be addressed while maintaining a well-
tuned database? Discuss briefly.
(b) Discuss the importance of Data volume and usage analysis for physical design.
17. (a) Discuss the power of controller under OFFENCES' of chapter XI.
(b) Discuss the various objectives of the IT Act 2000.
18. (a) What do you mean by Flowchart? Discuss benefits and limitations of flow chart.
(b) Draw a flow chart to compute and print for 25 transactions (assuming all are correct).
The Gross Sales (GS)
Discount Allowed (DA), and Net Sales (NS).
The input document shall provide the Quantity Sold (QS) and the Unit Price (UP). The discount is allowed as under :
No. of units sold Discount admissible
Less than 100 Nil
100-200 2%
201-500 5%
501-1000 10%
More than 1000 20%
Calculate Gross Sales, Discount allowed and Net Sales and must be printed on every page.
19. (a) Discuss various types of Decision Table in brief.
(b) The details of procedure for dealing with delivery charges for goods bought from Jindal and Company Ltd. is given below :
For calculating the delivery charges, customers are divided into two categories, those whose sales region code is 10 or above and those with the code of less than
10.
If the code is less than 10 and the invoice amount is less than Rs. 10,000, the delivery charge to be added to the invoice total is Rs. 200. But if the invoice value is for Rs. 10,000 or more, the delivery charge is Rs. 100.
If the code is equal to or greater than 10, the corresponding delivery charges are Rs. 250 and Rs. 150 respectively.
Prepare a decision table of the above procedure.
Word Processing
20. (a) Write various steps involved to performs Mail Merge. (b) Discuss in brief various features of tables in MS-Word.
Spread Sheet
21. (a) Write the steps to create the Macro in Excel 2000.
(ii) INT(x) (iii) COUNTIF (iv) ABS
(b) (i) FV (v) SUM
(vi) LEN (vii) DMAX (viii) UPPER
(ix) PROPER (x) CLEAN Business Project Management
22. (a) Discuss in brief various views in MS Power Point to create presentation in effective
manner.
(b) Explain the following concept in Ms-Power Point.
(i) Working with text
(ii) Working with slide master Computer Aided Audit Techniques
23. (a) Describe the various factors which determine the use of Computer Assisted Audit
Techniques (CAAT).
(b) Describe the Integrated Test facility (ITF) method used in conducting audit through computer.
Accounting Package
24. (a) Describe the various facilities to be provided by the user friendly accounting
software package.
(b) Explain the process of voucher entry in Tally 5.4 for the following:
(i) Purchase entry
(ii) Sales entry
25. Write short notes on the following.
(i) Bar Code Reader
(ii) Smart Card System
(iii) Diagnostic Routines
(iv) Wireless Networks
(v) Digital Signature
(vi) Web Casting
1. (i) Toggle: It is a switch or control code that turns an event on or off by repeated action or use. It also means to turn something on or off by repeating the same action.
(ii) Data Item: A set of characters which are used together to represent a specific data element e.g., a name item contains the alphabetic characters in a name, and an amount item contains the numerics in an amount.
(iii) EBCDIC system : With EBCDIC, each eight bit byte is divided into two portions-zone portion and the digit portion. The bits in both the zone portion of byte and the digit portion of byte are assigned numeric values based upon their binary number system, forming the basis for a logical representation of data in storage. Numeric values are represented in EBCDIC with all zone bits "on and the proper combination of bits in the digit portion of the byte "on to represent the particular value. For example value 4 is represent in the following manner,
1 1 1 1 0 1 0 0 Zone bit on digit bits
(iv) Accumulator: It refers to a storage area in memory used to accumulate totals of units or of amounts being computed.
(v) CMOS (Complementary Metal Oxide Semiconductor) : Personal computer uses the CMOS memory to store the date, time and system setup parameters. These parameters are loaded every time the computer is started. It is powered by lithium ion battery.
(vi) Cursor: A symbol that marks the current position of the mouse on the screen or the point of entry of data is referred to as cursor.
(vii) PCI slots: The PCI (Peripheral Component Interface) slots are used for connecting PCI based devices like sound cards, internal modems and graphics accelerator cards.
(viii) Intelligent Terminal: It has an in-built processing capability. It is also user-programmable. In addition to the storage areas, it has a microprocessor, which can be programmed to communicate with and instruct the user who is entering data.
(ix) Drag: It refers to the activity of moving something around the computer monitor with the help of the mouse. Dragging involves holding down one of the mouse buttons while the user moves it.
(x) Duplex Printing: Printing on both sides of a paper at the same time is called Duplex Printing.
(xi) Overlay : It is a technique which makes it possible to execute programs which are too large to fit into the computer's internal storage at one time. The program is segmented and two or more segments occupy the same internal storage location at different times during execution of the program.
(xii) Seek Time: Seek time is the time required to position a movable read-write head over the recording track to be used. If the read-write head is fixed, then seek time will be zero.
(xiii) Object program: It refers to a program expressed in a machine language, which can be directly executed by a particular computer. A compiler takes source program as an input and produces the object code/program.
(xiv) Debug: Error in a programme is called a bug and the process of finding and correcting the errors in a source programme is called debug.
(xv) Interpreter: It refers to a language translator that converts source program written in high level language to machine code and executes it immediately statement by statement.
(xvi) Structured Query Language (SQL): It refers to a set of commands for creating, updating and accessing data from a data base. It also aids the manager to make ad hoc queries from the database.
(xvii) Client: It is a software that is used to contact and obtain data from a server software program on another computer, often across a great distance. Each client program is designed to work with one or more specific kinds of server programs. A web browser is a specific kind of client.
(xviii) Multiplexer : This device enables several devices to share one communicator line. It scans each device to collect and transmit data on a single line to the CPU. It also communicates transmission from the CPU to the appropriate terminal linked to the multiplexer.
(xix) Bridge: The main task of a bridge computer is to receive and pass data from one LAN to another. In order to transmit this data successfully, the bridge magnifies the data transmission signal. This means that bridge can act as a repeater as well as a link.
(xx) FTP: FTP refers to File Transfer protocol. It is a common method of moving files between two Internet sites. There are many publicly accessible sites from where information can be obtained using FTP.
(xxi) Uniform Resource Locators: Uniform Resource Locators are used by Web Browsers to address and access individual web pages, web sites and Internet resources. The format of a URL is as given below:
Protocol/Internet address/web page address
Example : http://www.icai.org/seminars.html
(xxii) PPP (Point-to-Point Protocol) - It is most well known protocol that allows a computer to use a regular telephone line and a modem to make TCP/IP Internet connection and thus be really on the Internet.
(xxiii) Internet Service Provider (ISP): An institution that provides access to the Internet subscriber on a charge basis is referred to as Internet Service Provider. For example, in India VSNL (Videsh Sanchar Nigam Limited) is one of the Internet Service Providers.
(xxiv) Asymmetric Crypto System; It refers to a system of a secure key pair consisting of a private key for creating a digital signature and a public key to verify the digital signature.
|
2. (i) (324.25)10 = ( )2 | |||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||
|
= (101000100.01)2 (11101101.0101)2 = ( |
Fractional Value .25 X 2 = 0.50 0.50 X 2 = 1.0
10
(11101101.0101)2 = 1 x 27+1 x 26 + 1 x 2 5 + 0 x 24 + 1 x 21 + 1 x 22 + 0 x 21 + 1 x 20+ 0 x 2 _1 + 1 x 2 ~2 + 0 x 2 ~3 + 1 x 2
Now we need to regroup each 3-bit Binary form into 4-bit Binary form as follows:-= 1101 0010 0011 Heance, (6443)a = (D23)16
(iv) (568.5)10 = ( )8
|
8 |
568 |
Remainder |
|
8 |
71 |
0 |
|
8 |
8 |
7 |
|
8 |
1 |
0 |
|
0 |
1 |
= (1070.4)8
Fractional Value 0.5 X 8 = 4.0
(v) (292A)16 = ( )10
(292A)16 = 2x163 +9x162+2x161+10x160
= 2 x 16 x 256 + 9 x 256 + 2 x 16 + 10 = 8144 + 2304 + 32 +10 = (10490)10 = (10490)10 = ( )8
Hence, (292A)16
(vi) (10110101.11)2
To convert the given number from Binary number system to Octal number system, each digit of the number will be represented in groups of three bits, adding leading or trailing zeros wherever required.
(10110101.11) = 010 110 101 . 110
= 2 6 5 . 6
Hence, (10110101.11)2 = (265.6)8
(vii) (6DAF)16 = ( )2
To convert the given hexadecimal number to binary, each digit of number will be represented in Binary form using a group of four bits.
(6DAF) = (0110 1101 1010 1111)
Hence, (6DAF)16 = (110110110101111)2
(viii) (1001011.110101)2 = ( )16
To convert the given number from Binary number system to Hexadecimal number system, each digit of the number will be represented in a group of four bits, adding leading or trailing zeros wherever required.
(1001011.110101)2 = (0100 1011. 1101 0100)
= (4B D4)
Hence, (1001011.110101)2 = (4B D4)16
(ix) (CD.1C)16 = ( )8
To convert the given number from Hexadecimal Number System to Octal Number System, each digit of the number will be represented in Binary form using a group of four bits.
(CD.1C) = 1100 1101 0001 1100
Now we need to regroup each 4-bit Binary form into 3-bit Binary form as follows:-= 011 001 101 000 011 100 = 3 1 5 0 3 4 Hence, (CD.1C)16 = (315.034)8
(x) (310.04)8 = ( )2
To convert the given number from Octal number system to Binary number system, each digit of the number will be represented in binary form.
= 011 001 000. 000 100
(310.04)8 = (11001000.0001)2
3. (i) Use of Master files: A master file contains relatively permanent records for identification and summarising statistical information. A product file, customer file and employee file are examples of master files. The descriptive information in a master file may include such items as product code, descriptions, specifications, etc.
(ii) Use of Data Bus: The Data Bus is an electrical path that connects the CPU, memory, and other hardware devices on the motherboard. Actually, the bus is a group of parallel wires which carries data on high speed. More the number of wires, more the data speed.
(iii) Use of Parallel Ports: Parallel ports are used to connect external input/output devices like scanners or printers. Parallel ports facilitate the parallel transmission of data, usually one byte at a time. Parallel ports use 25 pin RS 232C.
(iv) Use of Integrated Circuits: It is made up of very thin silicon chip which contains a number of small storage cells that can hold data. Instead of being made up of a series of discrete components, these units are constructed as integrated circuits, meaning that a number of transistors are integrated or combined together on a thin silicon wafer to form a complete set of circuits. The faster and more expensive bipolar semi conductor chips are often used in the ALU and high speed buffer storage sections of the CPU, while the slower and less expensive chips that
employ metal-oxide semi-conductor technology are used in the main memory section.
(v) Use of Disk Formatting: A new diskette is nothing more than simple coated disk encased in plastic. Before the computer can use it to store data, it must be magnetically mapped into tracks and sectors called formatting so that the computer can go directly to a specific point on the diskette without searching through data.
(vi) Use of Spooling Software: The purpose of spooling is to compensate for the speed difference between the computer and its peripheral devices. These programs take the results of computer program and move them from primary memory to disk. The area on the disk where the program results are sent is commonly called the output spooling area. Thus, the output device can be left to interact primarily with the disk unit, not the CPU. It can also be used on the input side.
(vii) Use of Modem: Modem stands for modulator/demodulator. It is a device that converts a digital computer signal into analog telephone signal or vice versa. Modems are required to tele-communicate computer data with ordinary telephone lines because computer data is in digital form but telephone lines are analog.
(viii) Use of Hub: A hub is a hardware device that provides a common wiring point in a LAN. Each node is connected to the hub by means of simple twisted pair wires. The hub then provides a connection over a higher speed link to other LANs, the company's WAN or the Internet.
(ix) Use of Firewall: Firewalls are hardware and software systems that control the flow of traffic between the Internet and organization's Local Area Network and systems. These are set up to enforce specific desired security policies of the organizations. Firewall is an effective means of protecting the firm's internal resources from unwanted intrusion.
(x) Use of Intranet: Intranet is a means of intra-office communication. It facilitates communication within the organization and connects people together with Internet-technology in a single view. Through the Intranet, access to all information, applications and data can be made available through the same browser.
(xi) Use of Auxiliary storage devices: When user enters the data/program using input device, those are stored in RAM. RAM is a Volatile memory which means that all the contents of RAM are erased when the power is switched-off. Therefore, in order to store the entered data permanently for future reference, auxiliary memory is required. Auxiliary storage devices like Floppy disk, Magnetic disk and Magnetic tape have auxiliary memory.
(xii) Use of Boot strap loader: When a computer is first turned on or restarted, a special type of absolute loader called a bootstrap loader is executed. This bootstrap loads the first program to be run by the computer - usually an operating
system. Since no program can be executed without OS, hence bootstrap loader is the most essential system software without which the computer cannot be started.
(xiii) Use of Language Translator; Computer understands only binary language or machine language. Therefore, in order to convert assembly language program or source program to object program, language translator is required. Assembler, Interpreter and compiler are known as language translators.
(xvi) Use of Repeaters: Repeaters are devices that solve the snag of signal degradation which results as data is transmitted along the cables. It boosts the signal before passing it through to the next location.
(xv) Use of Router: Router is a special purpose computer or software package that handles the connection between two or more networks. Routers spend all their time looking at the destination addresses of the packets passing through them and deciding on which route the packets should be sent.
4. (i) Third Generation and Fourth Generation Languages
Third Generation Languages are called procedural languages and they are procedure oriented. They employ plain English like and mathematical expressions. They are intended for professional programmers, and require specification of how to perform task. Programmes written in third generation languages are also difficult to debug and usually translated through compiler. Code is difficult to learn, understand and maintain. These languages were originally developed for batch operations and are typically file oriented. FORTRAN, COBOL etc. are examples of third generation languages.
Fourth Generation Languages(4GLs), on the other hand, can be used by both programmers and non-programmers. 4GL uses English like instructions, has limited mathematical manipulation capability. It offers automatic report formatting, sequencing and record selection by user given criteria. However, 4GLs are less efficient than third generation languages. They require specification of what task to perform and the system determines how to perform that task. 4GL requires fewer instructions, code is easy to maintain and understand. Many features of 4GLs can be learned quickly. 4GLs are more structured and are data base oriented. Generally, these are available in two types (i) Production Oriented and (ii) User Oriented.
(ii) Dynamic RAM and Static RAM : The memory system constructed with MOS elements that can be changed is called RAM. The purpose of RAM is to hold programs and data while they are in use.
Dynamic RAM is the most common type of main memory. It is dynamic because each memory cell loses its charge so it must be refreshed hundreds of times each second to prevent data from being lost. The most popular DRAM used in desktop systems are Extended Data Out DRAM, Synchronous DRAM and Rambus DRAM. RDRAM sends data down at high-band width channel.
Static RAM, on the other hand, is a lot faster, larger and more expensive. It is static because it need not be continually refreshed. Because of its speed it is mainly used in cache memory.
The static RAM retains the stored data as long as power remains on, whereas in dynamic RAM the stored information is to be recharged before it disappears. The power consumption of dynamic RAM is less than static RAM. In DRAM, the computer does the refreshing process taking time out from other chores every millisecond. Dynamic RAM is the most common type of main memory whereas static RAM is faster, larger and more expensive than DRAM. Static RAM is used mainly in a special area of memory called a cache.
(iii) Control unit and Arithmetic logic unit: Control Unit supervises the entire operation of the computer system. It selects the program statements from the storage unit, interprets the statement and sends the appropriate electronic impulses to the ALU and storage unit to cause these units to carry out the operations required. Thus control unit does not perform the actual processing operations on data. Rather, its function is to maintain order and direct the flow of sequence of operations and data within the computer. Control unit also instructs the input devices, when to start and stop transferring data to storage unit and tells the storage unit when to start and stop transferring data to output devices. Hence, it acts as a central nervous system for component parts of the computer.
On the other hand, Arithmetic Logic Unit actually performs mathematical calculations, compares numeric and non-numeric values and makes decisions. Data flows between ALU and the storage unit during processing. Specifically, data is transferred as needed from the storage unit to the ALU, manipulated and returned to the storage unit.
(iv) Personal Computing and Network Computing
Personal Computing: The philosophy behind personal computing is that a computer should be readily available to an individual to perform his/her work at any time. Many tasks are individual by nature. Over the time, the range of tasks that a personal computer can accomplish has steadily increased largely because of the increasing availability of high-quality software. Some smaller businesses rely only on personal computers for all of their accounting, inventory management, customer database and transaction processing operations.
Network Computing: In network computing arrangement, individuals do their own work on personal computers, but are connected to other computers through a telecommunication network that allows them to share information and resources with others. Users in these environments may share databases, memos and other messages, and work in progress. They can also share printers, fax machines and links to external data sources. Providing duplicates of these resources for each of the members of the work group can be very costly for many organizations. Sharing of resources saves lot of cost for the organization.
(v) Impact Printers and Non-impact Printers: Impact printers use some form of striking device such as revolving print chains, rotary print wheels or wire-matrix printers. Non-impact printers use technology such as xerography or laser to produce output. Impact printers form images when electronic pulses activate printing elements that are pressed against an inked ribbon and form an image on paper. The characters to be printed are formed either by whole alphanumeric images or by dot matrix method, which arranges a series of dots to assume the shape of each character being printed. These printer fall into two categories i.e. serial printers and line printers. Non-impact printers use thermal, chemical, electrical or optical technique to form images. Thermal printers, ink jet printers and laser printers fall under this category.
Non-impact printers are much faster than impact printers because they involve less physical movements of parts. A speed of 3800 lpm (lines per minute) is very fast for an impact printer but speeds of upto 21,000 lpm are offered with some non-impact printers. Non-impact printers are capable of a wide range of fonts and quality approaching that of multilith book printing. However, only one copy of the document can be printed at a time. These printers are generally too expensive and give high-speed, high quality printing in comparison with impact printers. Impact printers, on the other hand are capable of printing multiple copies of a document , these are less costly and are mostly used where draft quality print is required.
(vi) CD-ROM and ROM-BIOS: CD-ROM stands for Compact Disc - Read Only Memory. It is an auxiliary storage device which is used to store large volumes of data and text. CD-ROMs are often used for the distribution of computer programs / softwares and user manuals. Using CD-ROM, the content can be read into primary storage for processing or display. However, the data on the disk are fixed, they cannot be altered.
ROM-BIOS stands for Read Only Memory - Basic Input Output System. It contains a set of instructions which perform the basic control and supervisory operations for the computer. These instructions are needed frequently by the computer system (to provide basic input/output services) and are not available in the computer circuitry.
(vii) Multi-programming and Multi-tasking systems: Multiprogramming is a
processing mode in which several partially completed programs are processed concurrently. At any given moment, only one program or job is actually being executed, but within a larger time span of several minutes, the computer is processing several jobs or programs, alternating between actually executing, and performing input/ output activities. Several jobs may be in memory but only one is being executed. When one job needs to do input/ output, another can begin (that is resume) execution. Thus two or more independent programs are executed in the same time span by interleaving their execution.
The advantage of multiprogramming is that overall performance of the system can be enhanced. The great speed of the central processing unit can be used and delays in waiting for input or output operations (a condition that is called, being input/ output bound) can be avoided.
Main frames and mini computers work in multi-user multiprogramming environment.
Multitasking is a logical extension of multiprogramming. Personal computers generally work in multitasking environment. It refers to the operating system's ability to execute two or more of a single user's task concurrently. Multiple tasks are executed by the CPU switching between them. The CPU scheduler selects a task from the ready queue and switches the CPU to that task. When time slot expires, the CPU switches from this task to another task. In this method, the CPU time is shared by different processes.
The main advantage of multitasking is efficient CPU utilization. It provides single user with multiprogramming capabilities.
(viii) System Software and Application Software: System Software comprises those programs that direct the computer in performing tasks that are basic to proper functioning of the computer system or commonly needed by system users. It includes (i) assemblers and compilers, (ii) diagnostic routines, (iii) utility programs,
(iv) supervisory programs, and (v) library of subroutines. The system software of one computer system may differ in many ways from that of another.
Application software directs the computer in performing specific user-related data processing tasks. Application programs fall in two categories viz., cross industry i.e. programs that perform tasks common to many industries or organisations and industry specific i.e. programs that perform tasks unique to a particular industry or organisation. The most popular application programs are used by individuals to improve the speed and quality of their work. Examples of such programs are payroll, general accounting, sales statistics, and inventory control etc.
Systems software is traditionally written in low-level languages. A detailed knowledge of system hardware is needed to write such programs. Hence, systems software are generally provided by the computer manufacturers or software development firms that specializes in writing systems program.
Application programs are either written by individual users in high-level language or written and marketed by service companies as generalised applications packages on modular design which can be tailor-made to cater to the needs of different users.
|
(ix) Sequential File Organization and Random File Organization | |||||||||
|
| |||||||||
|
(x) Online System and Real Time System |
Online Systems: Online system refers to processing of individual transactions as they occur from their point of origin as opposed to accumulating them into batches. This is made possible by such direct access devices as magnetic disk and number of terminals connected to, and controlled by a central processor. In this way, various departments in a company can be connected to the processor by cable. If operating companies are a number of miles away from the processor then they are linked by means of telegraph, telephone lines or even through satellite. This type of processing provides multi-access to information files by terminal users and also enables them to update files with transaction data. Some examples where online applications are being used are electricity and gas boards, banking system, tour operators, stock exchanges and for stock control.
Real Time systems: The term real time system refers to the technique of updating files with transaction data immediately after the event to which it relates occurs. Real time system is basically on-line system with one specialty in inquiry processing. The response of system to the inquiry itself is used to control the activity. Real time systems usually operate in multi programming and multi processing. This increases both availability and reliability of the system. CPU's in real time systems should possess capability of what is known as program interrupts.
Some of the leading areas for real-time applications are sales order processing, transport and travel reservation, manufacturing control system, and airline reservation system.
(xi) Local Area Network and Wide Area Network
Following are the salient features of LAN:
Multiple user computers are connected together.
Computers are spread over a small geographic region.
Communication channels between the computers are usually privately owned.
Channels are relatively high capacity and error- free.
LAN enables multiple users to share software, data, devices and physical media.
On the other hand, the salient features of WAN are as stated below:
Multiple user computers connected together.
Computers are spread over a wide geographic region.
Communication channels such as long distance telephone service, satellite transmission etc. are provided by third party.
Channels are relatively low capacity and error-prone.
WAN operates at lower link speed, usually 1 Mbps.
WAN does not allow sharing of resources.
(xii) Client-Server Architecture and Peer- to -Peer architecture: In Client-Server architecture, the network has certain machines and devices called servers that are specially dedicated to provide various services to the other computers called clients. Different types of specialized servers include file, fax, printer, modem, e-mail and database server. The most common type of client server arrangement is a LAN composed of microcomputers connected to a network server, which serves to all the clients (users) of the LAN. A client program running on one of the microcomputers can request specific data from the server. The server program retrieves the requested data from its databases and returns it to the client. This way, a LAN permits all the computers connected to it to share hardware, software and data.
On the other hand, in Peer-to-Peer architecture, there are no dedicated services. All computers are equal, and therefore, are termed as peer. Normally, each of these machines functions both as a client and a server. This arrangement is suitable for environments with a limited number of users. Moreover, the users are located in the same area and security is not an important issue while the network is envisaged to have a limited growth. At the same time, users need to freely access data and programs that reside on other computers across the network. The basic advantage of this architecture is simplicity of design and maintenance. Since there is no server, all nodes on the network are fully employed. Further, the network is not totally reliant on a particular computer and linking computers in a peer-to-peer network is more straightforward.
(xiii) Network-attached storage and Direct-attached storage: Network-attached storage (NAS) is a dedicated shared storage solution that attaches to a network topology, becoming immediately and transparently available as a network resource for all clients. NAS is platform and operating system independent. It can be attached without powering down the network, and requires no changes to the existing file servers. A NAS device is typically a stand alone, high performance, single-purpose system or component. It serves specific storage needs with its own operating system and integrated hardware and software. NAS devices are well suited to serve heterogeneous networks. They enable file and data sharing among different types of clients.
Direct attached storage (DAS), on the other hand, is a storage device that connects directly to a single server. Network workstations access the server to connect to this storage. Because the server may be handling distributed applications such as e-mail or databases, the performance of DAS is typically not as high as that of networked storage. DAS uses the security features of the server's network operating system.
(xiv) Audio Conferencing: It is the use of audio communication equipments which allow the user to communicate with geographically dispersed persons. Audio conferencing does not require a computer but requires a two way audio communication facility.
Guidelines to make Audio conferencing more efficient are as stated below:
(a) All the participants must have an opportunity to speak.
(b) Number of participants must be kept to manageable size.
(c) Copy of conferencing agenda must be sent to all the participants in advance through FAX.
(d) Participants must identify themselves.
(e) Conferencing discussion must be recorded.
(f) Hard copy of the discussion must be prepared and should be sent to all the participants for approval.
Video Conferencing: It is the use of television equipment which allow the user to communicate with geographically dispersed persons. The equipment provides both sound and picture. The participant can see and hear each other and it does not required computers. Participants gather in specially equipped rooms having audio and video facility.
There are three types of Video Conferencing:
(a) One way Video and Audio: In this case, audio and video is traveled only in one direction e.g. Television.
(b) One way Video and Two way Audio: In this case, audio is transferred in both directions but video is transferred in one direction e.g. Discussion of News Reader with field correspondent.
(c) Two way Video and Audio: In this case, audio and video is transferred in both directions between sender and receiver e.g. Discussion of persons between different studios of a News Channel.
(xv) Horizontal partitioning and Vertical partitioning : Horizontal partitioning breaks a data relation into multiple record specifications by placing different rows into different records based on common column value. It makes sense when different categories of rows of a table are processed separately. Horizontal partitioning is more secure as the file level security can be used to prohibit user from seeing certain rows of data. Also each partitioned table can be organized differently, appropriate for how it is individually used. Further each partitioned files can be placed on a separate disk driver to reduce contention for the same drive, hence improves performance across the database.
Vertical partitioning, on the other hand, distributes the columns of a relation into separate files, repeating the primary key in each of the files. An example of vertical partitioning would be breaking apart a part relation by placing the part number along with accounting related part data into one record specification, the part number along with engineering related part data into another record specification and the part number along with sales related part data into another record specification. The other advantages of vertical partitioning are similar to those of horizontal partitioning.
5. (a) There are 3 types of computer system based on the working efficiency. These are
(i) Analog computers, process data input in a continuous form. Data such as voltage, resistance or temperature and pressure are represented in the computer as a continuous, unbroken flow of information. analog computers are very useful in many systems. they are used to control processes in the food and the petroleum industries. As the measurements in analog computers are carried out by a few single purpose devices, the analog computer offers low cost and ease in programming. The main disadvantage of an analog computer is its accuracy factor, and the limited storage capacity. Hence it is not suitable for processing business data.
(ii) Digital computers, count and accept letters or numbers through various input devices that convert the data into electric pulses, and performs arithmetic operations on numbers in discrete form. In addition to performing arithmetic operations, they are also capable of (1) storing data for processing, (2) performing logical operations, (3) editing or deleting the input data and (4) printing out the result of its processed routine at high speed. One of the main advantages in the use of digital computers is that any desired level of accuracy can be achieved by considering as many places of decimal as is necessary and hence are most suitable for business applications. The main disadvantage of digital computers is their high cost and the complexity in programming.
(iii) Hybrid computers, are computers that comprise features of analog computers and digital computers. The digital component normally serves as the controller and provides logical operations, while the analog component normally serves as a solver of differential equations.
(b) Computer as an electronic data processing device capable of receiving input, storing sets of instructions for solving problems and generating output with high speed and accuracy. Computers are composed of switches, wires, motors, transistors and integrated circuits, assembled on frames. The frames form components such as keyboards, printers, visual display unit, disk drives, magnetic tape drives, and central processing units. These components are wired together into a network called a computing system, often called a computer.
Advantages of Computer System:
(i) Speed: Computer operations are measured in milliseconds, microseconds, nanoseconds, and picoseconds (one thousandth, one millionth, one billionth, and one trillionth of a second, respectively).
(ii) Accuracy: Errors do occur in computer-based information systems, but precious few can be directly attributed to the computer system itself. The vast majority can be traced to a program logic error, a procedural error, or erroneous data. These are human errors.
(iii) Reliability: Computer systems are particularly adept at repetitive tasks. Anything below 99.9% uptime, the time when the computer system is in operation, is usually unacceptable.
(iv) Memory Capability: Computer systems have total and instant recall of data and an almost unlimited capacity to store these data. A typical mainframe computer system will have many billions of characters stored and available for instant recall
Disadvantages of Computer systems:
(i) Program must be reliable: The computer does what it's programmed to do and nothing else. But a program that has operated flawlessly for months can suddenly produce nonsense. Perhaps some rare combination of events has presented the system with a situation for which there's no programmed course of action. Or perhaps the course of action provided by the programmer contains an error that's just being discovered.
(ii) Application logic must be understood: The computer can only process jobs which can be expressed in a finite number of steps leading to a specify goal. Each step must be clearly defined. If the steps in the solution cannot be precisely stated, the job cannot be done. This is why the computer may not be helpful to people in areas where subjective evaluations are important.
6. (a) Various features of the Central Processing Unit :
The various features of the Central Processing Unit are as follows:
(i) Clock Speed: The Clock Speed is the speed at which the processor executes instructions. Clock speed is measured in megahertz (MHz) which is a million cycles per second. Therefore, a 450 MHz processor performs 450 million instructions per second. Higher the clock's speed, the faster the processor, the
better the system performance.
(ii) Cache: Processors incorporate their own internal cache memory. The cache acts as temporary memory and boosts processing power significantly. The cache that comes with the processor is called Level One (L1) cache. Generally, more the L1 cache, faster the processor. Additionally, PCs also include a much slower secondary, or Level Two (L2) cache. This cache resides on the motherboard and delivers slower performance when compared with the L1 cache.
(iii) Architecture: The CPUs architecture determines the manner in which it processes data. New CPUs employ multi-staged pipelines for transmitting data. To ensure proper data flow through these lines, the CPU includes a kind of prediction and error correction mechanism.
(iv) Slot: Different processors use different sockets or slots to fit onto the motherboard. Based on the type of processors, there are two main types of slots for connecting to the motherboardSocket 7 and Slot 1. Socket 7 is a 321-pin socket for Pentium class CPUsPentium MMX, K5, and K6ranging from 75 MHz to 200 MHz processors. However, the Pentium II/III CPUs use Slot 1 for connecting to the motherboard.
(v) Density : A CPU is made up of millions of small transistors. A CPU performs all the calculation and manipulation operations by synchronising between the transistors. Therefore, the shorter the distance between two transistors on a CPU, the faster the performance.
(vi) MMX: MMX stands for Multimedia Extensionsa set of instructions built in to the CPU, specifically intended for improving the performance of multimedia or graphic applicationsmainly games.
(b) The CPU contains the basic instructions needed to operate the computer, but it does not have the capability to store programs or large sets of data permanently. Just like the human brain, which helps to determine what to do and when, computers need blocks of space that it can address from time to time to help in processing arithmetical and logical operations and also hold programs and data being manipulated. This area is called memory
Various Types of Memory used in computer systems are :-
(i) Semi-Conductor Memories are based on the principle of storage chips. This thin silicon chip contains a number of small storage cells that can hold data. Instead of being made up of a series of discrete components, these units are constructed as integrated circuits, meaning that a number of transistors are integrated or combined together on a thin silicon wafer to form a complete set of circuits. The faster and more expensive bipolar semi conductor chips are often used in the arithmetic-logic unit and high-speed buffer storage sections of the CPU, while the slower and less expensive chips that employ metal-oxide semi-conductor (MOS) technology are used in the main memory section. There are two types of built-in memory as follows:-
Permanent Semi-Conductor Memory: Permanent Semi-Conductor Memory always retains the data they hold even when the computer is turned off. This type of memory is called nonvolatile memories.
Non permanent Semi-Conductor Memory: Non permanent Semi-Conductor Memories are those memories which in fact lose their contents when the computer's power is shut off. These chips provide volatile storage. A back-up uninterruptible power system is thus desirable in installations with volatile semiconductor storage.
(ii) Random-Access-Memory (RAM) :The memory system constructed with metal-oxide semi conductor storage elements that can be changed is called a random access memory (RAM) . The purpose of RAM is to hold programs and data while they are in use. It is called random access memory since access time in RAM is independents of the address of the word, that is, each storage location (address) inside the memory is as easy to reach as any other location and takes the same amount of time. A random access memory is extremely fast but can also be quite expensive.
RAMs can be further divided according to the way in which the data is stored, into dynamic RAMs and static RAMs.
Dynamic RAM: Dynamic RAM (DRAM) is the most common type of main memory. It is dynamic because each memory cell quickly loses its charge so it must be refreshed hundreds of times each second to prevent data from being lost. Some of the types of DRAM are :
- Fast Page Mode (FPM) DRAM was used in most computers until EDO RAM came along.
- Extended Data Out (EDO) DRAM is slightly faster than FPM. One variation called burst EDO (BEDO) DRAM assumes that the next data - address to be requested by the CPU follows the current one so it sends that also.
- Synchronous DRAM (SDRAM) can synchronize itself with the clock that controls the CPU. This makes data transfers more reliable and faster because timing delays are eliminated. It is anticipated that this form of memory will replace EDO as the most common form of memor
- Rambus DRAM (RDRAM) is the latest design and Intel has announced that all of their future systems will require it. RDRAM is very fast, but the system must be slightly redesigned to use it. RDRAM sends data down a high-band width "channel 10 times faster than standard DRAM.
Static RAM: Static RAM (SRAM) is like DRAM but it's a lot faster, larger, and more expensive. It's static because it doesn't need to be continually refreshed. Because of its speed, SRAM is used mainly in a special area of memory called a cache.
The Static RAM retains the stored data as long as the power remains in, whereas with dynamic RAM, the stored information disappears after a few milliseconds have elapsed. The data must, therefore be repeatedly refreshed before it disappears. The power consumption of a dynamic RAM is less than that of a static RAM, which has the advantage of making a higher degree of integration possible. The computer does the refreshing process itself, taking time out from other chores every few milliseconds. It will read all the RAM memory positions while they are still readable and put appropriate new charge on each capacitor. Some dynamic RAM memory circuits include built-in "refresh circuits to relieve the computer.
(iii) ROM stands for Read Only Memory. This memory is used for performing the basic controls and supervisory operations for the computer. It also handles the basic needs of the hardware involved, which include all I / O devices. The information in ROM is stored permanently and hence it is referred to as a non-volatile memory. As the name implies, the information from the memory can be read out but fresh information cannot be written into it. Various types of Read Only Memory (ROM) are as follows:-
PROM: PROM stands for Programmable Read Only Memory. It is a non-volatile memory which allows the user to program the chip with a PROM write. The chip can be programmed once, there after, it can not be altered.
EPROM: EPROM stands for Erasable Programmable Read Only Memory. Unlike ROM and PROM chips, EPROM chips can be erased and reprogrammed. Data in EPROM is erased by exposing the chip to Ultra-violet light.
EEPROM: EEPROM stands for Electrically Erasable Programmable Read Only Memory. The data in EEPROM can be erased by applying electrical charges.
(iv) Bubble Memory : It is composed of small magnetic domains formed on a thin single-crystal film of synthetic garnet. These magnetic bubbles, which are actually magnetically charged cylinders, only a few thousandths of a centimeter in size, can be moved across the garnet film by electric charges. The presence or absence of a bubble can be used to indicate whether a bit is on' or off'. Since data stored in bubble memory is retained when power to the memory is turned off, it can be used for auxiliary storage. Bubble memory has high potential because of its low production costs and its direct access capabilities, thus it may become widely employed as main memory technology. Since it is small, lightweight, and does not use very much power, bubble memory is finding a great deal of use as an auxiliary storage in portable computers.
(v) Flash Memory: Flash Memory is a memory in which the data is recorded permanently and is not wiped out when the power is turned off. Flash memory devices are very fast because they do not have any moving part.
(vi) Video RAM: Video RAM (VRAM) is used to accelerate the display of graphics on the screen. It does this by using two "ports, one connected to the CPU and the other to the screen. Data flows in one port and out the other very smoothly.
(vii) Virtual Memory: A technique that allows the execution of a process, even though the logical address space requirement of the process is greater than the physical available main memory. The technique works by dividing a program on disk into
1
(iii) (6443)8
fixed length pages or into logical, variable length segments. Virtual memory thus extends primary memory by treating disk storage as a logical extension of the main memory.Virtual memory helps in efficient main memory utilization. The programs can be loaded partially in the main memory, so more programs can be run at the same time. Hence, efficient CPU utilization and better throughput is possible by using the concept of virtual memory. Virtual memory makes the task of programming much easier, because the programmer no longer needs to worry about the amount of physical or main memory available.
7. (a) Data and programs are transcribed from source documents to some magnetic media for inputting to the computer. Some of the data entry devices, which are used for transcribing source information on magnetic media are as follows.
(i) Keyboard encoding direct to magnetic tape (including verification). A keyboard is used by the operator, who, while reading from source documents depresses appropriate keys on the keyboard, causing the characters to be recorded on seven or nine-track magnetic tape. For verification, the encoder compares the recorded data when it is keyed in second time. This system has been replaced by key-to-disc systems.
(ii) Keyboard encoding CRT display (including verification). This method is more sophisticated than the basic one indicated above, even though a keyboard is used in a similar manner. The special features of this method are as follows:
As the operator keys data from source documents, it is displayed on a CRT, thereby enabling her to check her work visually. In this case, data preparation also includes verification.
To enable keyboard errors to be reduced, magnetic tape cassettes can be supplied which have a special format for display on the CRT as a visual replica of the source document. The operator then keys in the information as if completing a form on a typewriter.
Pooling is possible, whereby a maximum of twelve operators can key into up to four tape drives.
(iii) Key to-disk system consists of a mini processor, number of keying stations, supervisor console and a magnetic disk. Keying station consists of a keyboard and VDU. Supervisor's console is used to monitor the functioning of different operators working on different keying stations, usage of magnetic disk and status of Input data.
Each keying station is connected to the mini processor and for each keying station, fixed area of main memory in the mini processor is allocated. When the data is entered from a keying station, it is stored in its allocated area. When the allocated area in the mini processor is filled with data, then the data from that area is shifted on the magnetic disk as a record. Key-to-disk system provides accuracy of input, security and monitoring of progress. However, since all the keying stations are connected with a single mini processor and in case mini processor fails, then all keying stations stop working.
(iv) Key-to-diskette stand-alone computers are provided to the different operators for data entry. Data entered by them is stored on the floppy disks. The data recorded on the floppy disks are later transferred to magnetic tapes with the help of data converter. The data converter can handle upto 20 diskettes at a time.
Since all the computers used are stand-alone computers, therefore, if one computer fails, it will not stop the working of others. In addition to this, stand-alone computers can be installed close to the source of data. Key-to-diskette system allows decentralized recording of data and centralized conversion on magnetic tape for processing by a mainframe computer.
(b) Screen Resolution :One of the most important features used to differentiate display devices is the clarity, or resolution, of the images that are formed on the screen. Most display devices form images from tiny dots - called pixels ( a contraction of the two words "picture elements) - that are arranged in a rectangular pattern. The more dots that are available to display any image on -screen, the sharper the image (the greater the resolution) is.
Various Types of Display Adaptors are:
Images are formed on monitor's screen by a card called the display adaptor card. If a user wishes to change the kind of display, e.g, from black and white to colour, the display adaptor card must be changed. The key elements of display adaptor cards the video controller and the memory.
(i) MGA - MGA or Monochrome Graphics Adapter is one of first adapters. It is a text -only adapter which generates very clear, easy-to-read characters. It works only with monochrome monitor.
(ii) CGA - CGA or Colour Graphics Adapter works in both text and graphics mode. It supports both colour and monochrome modes with various resolutions. However, it has relatively poor display quality in text mode. A CGA adapter provides following two combinations of resolutions
640 x 200 pixels with 16 colours.
320 x 200 pixels with 4 palettes.
Each of these palettes has 4 different colours. Only one palette can be used at a given time.
(iii) EGA - An EGA or Enhanced Graphics Adapter combines all features of a MGA & CGA with higher resolutions. It supports up to 16 colours at a time. An EGA usually has a high resolution of either 640 x 200 pixels or 640 x 350 pixels.
(iv) VGA - VGA or Video Graphics Adapter is a high quality graphics adapter which provides upto 256 colours and also a high resolution. Following are the two typical combinations of resolutions and colours that a VGA provides.
640 x 480 pixels with 16 colours.
320 x 200 pixels with 256 colours.
(v) SVGA- SVGA or Super Video Graphics adapter is an improvement on the VGA. The two combinations of resolutions and colours provided by SVGA are
640 x 480 pixels with 256 colours.
1024 x 480 pixels with 16 colours
8. (a) Various features of Chain Printer and Drum Printer: It has a chain that revolves at a constant speed in a horizontal plane. The complete chain has a complement of 48 numbers, alphabets and special symbols cast on 5 times over. It is confronted by a set of as many hammers as the number of print position say, 160. These hammers are magnetically controlled. The continuous stationery and ribbon are inter posed between a segment of the chain and the set of hammers. When a required character on the chain faces its print position, the corresponding hammer is actuated.
Drum Printers : These printers use a solid cylinder. There are as many bands on it as the number of print positions. Each band has cast on it the complement of 48 numerals, alphabets and special characters. The drum rotates at a constant speed confronted by a set of as many hammers as the number of bands with the inked ribbon and continuous stationery interposed. In one rotation of the drum there would be appropriate strikes by the set of the hammers. In the first strike A's are printed in
the appropriate print positions, followed by B,C,.......Z,0,1.........9 and special
symbols one by one.
(b) A non-impact printer forms characters by chemical or electronic means. Three types of non-impact printers are worth mentioning because they are expected to become more important in the future, as the technology becomes cheaper. These are thermal printers, ink-jet printers and laser printers. They are fast in operation, printing a page, or even more in a second but currently they are too expensive to be widely used.
(i) Thermal printers : Thermal Printers: Thermal Printers use thermal printing facility
i.e. the pins are heated by the electric element and then pressed against the paper. When the pins touch the paper, the area heated by the pins changes colour, usually to black or brown to form the character.
(ii) Ink-Jet Printers : This type of printers utilize the dot matrix principle but instead of pins, set mechanically to form a character, it uses an array of nozzles which spray jets of ink onto the paper. Inkjet printers are very quiet and provide laser-like quality at a much lower cost although supplies are relatively expensive. There are two types of inkjet printers:
Liquid inkjet : Color inkjet printers use three separate inkjets, one for each of the primary colors (red, green, and blue).
Solid inkjet: This produces an exceptionally high-quality image with sharp edges and good colour reproduction. Solid inkjet printers are also the best for producing low-cost but high-quality transparencies.
(iii) Laser Printers : Laser printer uses a combined system which utilizes laser and Xerographic photocopying technology. In a laser printer, a beam from a small laser scans horizontally across a charged xerographic selenium drum to build up an invisible electrostatic image of a whole page of text. Using standard photocopier techniques, the formed image is then transferred to the paper being printed. Toner is attracted to the electrostatic image and it is then permanently fixed using heat. The laser printer prints a page at a time. Its speed can be anywhere between 4 to 17 pages per minute (ppm). The resolution of laser printers is measured in dots per inch (DPI).
9. (a) Diskette Storage capacity depends upon the following factors:
(i) Number of sides of the diskette used: Earlier disks and drives were designed so that data could be recorded only on one side of the diskette. Now -a -days disk drives are manufactured so that data can be read/written on both sides of the diskette. Such drives are called Double Sided Drives'. The use of double sided drives and diskette approximately doubles the number of characters that can be stored on the diskette.
(ii) The recording density of the bits in the track: Recording density refers to the number of bits that can be recorded on a disk in one inch circumference of the innermost track on the diskette. This measurement is referred to as bits per inch (bpi). For the user, the diskette is identified as being either single density or double density. A single density drive can store 2768 bits per inch.
(iii) The number of tracks on the diskette: Number of tracks depends upon the drive being used. Many drives record 40 tracks on the surface of the diskette. Other drives, however, can record 80 tracks on the diskette.
In case of hard disk the storage capacity depends on the number of platters that are stacked on the top of one another, the number of tracks per platter and the number of sectors per track. Hard disks generally have 6 platters, i.e. 12 faces out of which eleven faces can be used. Each side may have 200 or more tracks, each track having 54, 63 or even more sectors per track and hard disk generally store 512 bytes of data in a sector. Data on magnetic disc is stored in cylinders where the nth track of each face vertically above and below each other constitutes cylinder n.
Thus, the storage capacity of hard disk is calculated as = No. of cylinders x no. of usable sides x No. of sectors / track x no. of bytes / sector.
(b) Optical Laser Disks
Optical laser disk storage is capable of storing vast amount of data. With this
technology, the read/write head used in magnetic storage is replaced by two lasers.
One laser beam writes to the recording surface by scoring macroscopic pits in the
disk, and another laser reads the data from the light sensitive recording surface. A light beam is easily deflected to the desired place on the optical disk, so a mechanical access arm is not needed.
There are three main categories of optical laser disks.
(i) CD-ROM stands for Compact Disc - Read Only Memory. It is an auxiliary storage device which is used to store large volumes of data and text. CD-ROMs are often used for the distribution of computer programs / softwares and user manuals. Using CD-ROM, the content can be read into primary storage for processing or display. However, the data on the disk are fixed, they cannot be altered.
(ii) WORM Disks: It stands for write once, read many optical laser disks, or WORM disks. These are used by end user companies to store their own proprietary information. Once the data have been written to the medium, they only can be read, not updated or changed. The PC version of a WORM disks cartridge, which looks like a 5% inch version of the 31/2 inch diskette, has a capacity of 200 MB. Access times for CD-ROM and WORM drives tend to be quite slow by hard disk drive standards, ranging from 100 to 300 milliseconds. The WORM disks cartridge is a feasible alternative to magnetic tape for archival storage; for example, a company might wish to keep a permanent record of all financial transactions during the last year. Another popular application of WORM disks is an information system that requires the merging of text and images which do not change for a period of time.
(iii) Magneto-Optical Disks : Magneto-optical integrate optical and magnetic disk technology to enable read-write storage. The 5% inch disks store up to 1000 MB. Magneto-optical disks are too expensive and do not offer anywhere near the kind of reliability that users have come to expect of magnetic media. In addition, the access times are relatively slow, about the same as a low-end Winchester disk.
As optical laser disk technology matures to offer reliable, cost - effective, read/write operation; it eventually may dominate secondary storage in the future as magnetic disks and tape do today.
This optical drive uses thermo-magnetics of magneto optical recording to ensure the integrity of data.
(iv) Video Disks: A video disk can store text, video, and audio data. Video disks can be accessed a frame at a time or played like a phonograph record. The advantages of DVDs are therefore self-evident - a huge storage capacity that enables users to archive large amounts of data on a single, lightweight, removable, reliable, easily-transportable medium. VDDs are now used mostly for entertainment - for example, storing video movies or large amounts of prerecorded music- experts predict that DVDs will become the medium of choice for distributing software or archiving large amounts of accounting data.
Video disks were first introduced in 1983, as a video game product. Today, however, they can provide companies with a competitive advantage.
Video disk systems were developed to help real estate agents conduct better searches for homes and properties for their clients.
Video disks are widely used for training applications. At a growing number of companies are using video disk systems take on such training tasks as showing how to boost factory performance, helping service technicians do a safer and better job, and training clerks to analyze insurance applications.
10. (a) OS perform the function at two different levels, the hardware level and the user level. The interaction of the OS with the computer's hardware level is, for the most part, hidden from the user.
Even so, the user will, at some stage or another, wish to install programs/ applications, copy files, perform search routines or execute any one of a wide and ever-increasing range of tasks. In order to carry out these procedures, the user has to access and operate an appropriate user interface. However, before doing so, the user should have an appreciation of the significance of files and directories at the operating system level.
File names : A file is a collection of related data, saved on a specific area of the surface of whatever storage medium the system is using. To be accessed, the file must have a name which is recognised by the system. The name is also significant in that it is usually an indication of purpose of the file and the type of data stored in the file. For most OSs the file usually has two names. These are known as the prefix and the suffix / extensions. The prefix is supplied by the user. The suffix is supplied by either the user or the computer application currently being used.
The prefix is frequently separated from the suffix by a full stop or a slash. For example, in a DOS or Windows environment, the file LETTER.TXT would suggest that it is a letter file containing text data. Below is a listing of some typical DOS/ Window file names with appropriate suffixes indicating their contents:
|
File Name |
Data Type |
|
PAY.BAS |
Basic program (.BAS - Basic) |
|
COMP.WKS |
Spreadsheet data file (.WKS -Worksheet) |
|
ACC.CBL |
Cobol program(.CBL - Cobol) |
|
FRED.DAT |
Simple data file (.DAT-Data) |
|
SAVE.BAT |
Batch file (.BAT -Batch file) |
|
NOTE.TXT |
Text file (.TXT- Text) |
|
LETTER.DOC |
Document file (.DOC - Document) |
|
MENU.EXE |
Executable file (.EXE - Executable) |
|
PROG.COM |
Command file (.COM - Command) |
|
REG.DBS |
Database file (.DBS - Database) |
|
PIC.IMG |
Image file (.IMG- IMAGE) |
Directories : A directory is like a drawer in a filing cabinet. It contains files. In addition, just as a filing cabinet usually consists of multiple drawers, similarly a computer disk usually contains multiple directories. A directory can, if necessary, also contain other directories. The purpose of directories is to enable the user to partition the computer's disk/storage devices in an organised and meaningful manner.
(b) Language Translators: It is a general term used for any assembler, compiler or other routines that accept statements in one language and produce equivalent statements in another language. The language processor reads the source language statements one at a time and prepares a number of machine instructions to perform the operations specified or implied by each source statement
There are three types of language translators:
(i) Compiler: It is system software, which is used to translate source codes to object codes. It scans the complete source program to find the syntax errors of the program and declares all those errors at the end of the compilation run. Once the user corrects all the errors, it then generates executable codes.
(ii) Interpreter: It is a system software, which is also used to translate source codes to object codes. It scans the lines of source program one by one. If there is an error in a line of source program, then it declares that error before proceeding to the next line. Therefore, it becomes necessary for the user to correct that error before finding errors in the remaining program, if any.
(iii) Assembler: It is a system software which is used to translate assembly language program to object code. First, the high-level language is translated to assembly language; then, using an assembler, it is converted to machine language.
11. (a) Best File Organization: The selection of best file organization for a particular application depends upon the following factors:
(i) File Volatility: It refers to the number of additions and deletion to the file in a given period of time. Applications which require large number of addition/deletion are called high volatile. An ISAM file would not be a good choice in such situation, since addition would have to be placed in the overflow area. Sequential file organization would be appropriate if there were no interrogation requirements.
(ii) File Activity: It is the proportion of master file records that are actually used or accessed in a given processing run. At one extreme is the real-time file where each transaction is processed immediately and hence at a time only one master record is accessed. Direct access organization is best suited here. At another extreme, for a payroll master file where almost every record is accessed when the weekly payroll is processed. A sequential master file would be more efficient in this case.
(iii) File Interrogation: It refers to the retrieval of information from a file. If the retrieval of records must be fast to support a real time operation then direct organization is more efficient. If the requirements for data can be delayed, then all the individual
requests can be batched and run in a single processing run with a sequential file organization. Large files that require many individual references to records must be organized under some type of direct access method. However, in small files, it may be more efficient to search the entitle file sequentially or with a more efficient binary search, to find an individual record than to maintain complex indexes or direct addressing scheme.
(iv) File Size: Large files that require many individual references to records with immediate response must be organized under some type of direct access method. But, with small files, it may be more efficient to search the entire file sequentially or with more efficient binary search, to find an individual record than to maintain complex indexes or complex direct addressing scheme.
(b) Data access and Organisation Methods
Organizing data involves arranging data in storage so that they may be easily accessed. Accessing data refers to retrieving data from storage. Data organization and access are important determinants of how easily managers and users can obtain the information they need to do jobs. Since some organisation and access schemes provide faster or more flexible ways to locate individual records than others, it is important for managers to anticipate what data they - and their subordinates - will need when designing files and databases.
There are two principal ways to access data: sequentially or directly. Sequential access refers to accessing records in the sequence in which they are physically stored. Direct access refers to accessing data in a manner that is relatively independent of the way the data are physically stored. Direct access is any type of access that does not require scanning all the records that precede a desired one. With direct access, individual records in a file can be accessed at random, in no particular order or sequence.
In Sequential file access, records are arranged one after another, in a predetermined order. For instance, the file in is organized sequentially by customer number. If this file were stored on a disk or tape, record 101 would physically be the first record in the file, followed by record 102, and so on.
CUSTOMER- NUMBER CUSTOMER- NAME
101
102
104
109
110
115
116 120 121
123
124
Sunil Arora Raman Kumar Sonia Gupta Suresh Sahni Raj Malhotra John Methews Uma Dalmia Mohan Kapoor Shaleen Bhutani Umesh Gupta Harish Varma
The field on which records are sequentially organized is often called the primary key. The primary keys have a unique value that can be used to access individual records in the file.
A common operation performed in MIS organisation is a sequential batch update, in which the transaction file is organized sequentially and the master file is accessed sequentially.
12. (a) The file processing system is still being used, but it has several problems that limit its efficiency and effectiveness for end user applications. These are stated below:
(i) Data Duplication: Independent data files include a lot of duplicated data; the same data such as customer's name and address is recorded and stored in several files. This data redundancy causes problems when data has to be updated, since separate file maintenance programs have to be developed and coordinated to ensure that each file is properly updated.
(ii) Lack of Data Integration: Having data in independent files makes it difficult to provide end users with information for ad hoc requests that require accessing data stored in several different files. Special computer programs have to be written to retrieve data from each independent file. This is difficult, time consuming and expensive for the organization.
(iii) Data Dependence: In file processing system, major components of a system i.e. the organization of files, their physical location on storage, hardware and the application software used to access those files depend on one another in a significant way. Application programs typically contain references to the specific format of data stored in the various files they use. Thus, if changes are made in the format and structure of data and records in a file, changes have to be made in all programs that use this file. This program maintenance effort is a major burden of file processing system.
(iv) Other Problems: Data elements such as stock numbers and customer address are generally defined differently by different end users and applications. This causes serious inconsistency in the development of programs, which access such data. In addition, integrity of the data is suspected because there is no control over their use and maintenance by authorized end users.
(b) Components of database environment
(i) The Data base files: These files have data elements stored in database file organisation formats. The data base is created in such a way so as to balance the data management objectives of speed, multiple access paths, minimum storage, program-data independence, and preservation of data integrity.
(ii) A data base management system (DBMS): A DBMS is a set of systems software programs that manages the data base files. The DBMS accesses the files, updates the records, and retrieves data as requested. The DBMS ensures that only those areas are accessed for which clearance has been granted. The DBMS has the
responsibility for data security which is vital in a data base environment since data base is accessed by many users.
(iii) The users: Users interact with the data base management system indirectly via applications programs or directly via a simple query language. This language enables the user to retrieve data in logical formats on an ad hoc basis. The user's interaction with the data base management system includes the definition of the logical relationships in the database, in put and maintenance of data, changing and deletion, and manipulation of data.
(iv) A host language interface systems: This is the part of the DBMS that communicates with the applications programs. The host language interface interprets instructions in high-level language applications programs, such as COBOL and BASIC programs that request data from the files so that the data needed can be retrieved.
(v) The application programs: These programs perform almost the same functions that they do in a conventional system, but they are independent of the data files and use standard data definitions. This independence and standardization make rapid special purpose program development easier and faster. Application programs, using the host language interface, are usually developed by professional programmers.
(vi) A natural language interface systems: The query language (e.g. SQL) permits online update and inquiry by users who are relatively unsophisticated about Computer Systems. This language is often termed English-like' because instructions of this language are usually in the form of a simple command in English, rather than consisting of symbols and equations. Most of the commands of query languages are pre-programmed and are activated when the user keys in combinations of English words to accomplish an inquiry task. Query languages also permit online programming of simple routines by managers who wish to interact with the data.
(vii) The data dictionary / directory : Data dictionary is a centralized depository of information, in a computerized form, about the data in the database. The data dictionary contains the scheme of the data base i.e. the name of each item in the data base and a description and definition of its attributes along with the names of the programs that use them, and who is responsible for the data; authorisation (access) tables that specify users and the data and programs authorised for their use.
(viii) Online access and update terminals: These may be adjacent to the computer or even thousands of miles away. They may be dumb terminals, smart terminals, or microcomputers.
(ix) The output system, or report generator: This provides routine job reports, documents and special reports. It allows programmers, managers and other users to design output reports without writing an application program in a
13. (a) Decision Support Systems: These are information processing systems which help the managers in decision making process. Advancement in hardware technology, interactive computing design graphics capabilities and programming languages has helped in the development of decision supports systems. These systems support management decision making process by solving relatively unstructured problems. A friendly computer interface eases the communication between the user and the decision support system.
Characteristics of Decision Support Systems :
(i) Decision support system support management decision making - It is mostly used for management planning decisions by the top managers. The same methods can be used by the operational managers to solve problems.Decision support systems enhance decision quality. While the system might point to a particular decision, it is the user who ultimately makes the final choice.
(ii) Decision support systems solve relatively unstructured problems - problems that do not have easy solution procedures and therefore problems in which some managerial judgment is necessary in addition to structured analysis. Because managers must plan for future activities, they rely heavily on assumptions of future interest rates, inventory prices, consumer demand, and similar variables.A key characteristic of many decision support systems is that they allow users to ask what-if questions and to examine the results of these questions. Decision support systems are useful in supporting this type of analysis. Decision support systems are much more flexible and may handle many different types of problems.
(iii) Finally, a friendly computer interface is also a characteristic of a decision support system - Because managers and other decision makers who are non programmers frequently use decision support systems, these systems must be easy to use. The availability of nonprocedural modeling languages eases communication between the user and the decision support system.
(b) Artificial Intelligence is a software that tries to emulate aspects of human behavior, such as, reasoning, communicating, seeing and hearing. AI software can use its accumulated knowledge to reason and, in some instances, learn from experience and thereby modify its subsequent reasoning. There are several types of AI, as discussed below:
(i) Neural Networks (NN): These are computing systems structured to emulate the brain's learning process. Like the brain, NN use interconnected processors that perform many operations simultaneously and interact dynamically to learn from data as it is processed. Although NN do not handle unexpected event very well, they are very good at recognizing patterns that humans overlook and at uncovering emerging trends. Like humans, NN learn by fine-tuning their accumulated knowledge using the facts present in each new case.
(ii) Voice Recognition System (VRS): VRS present the user with a hand-free voice-interactive computer interface. In other words, the users can discard conventional input devices such as keyboard or mouse, and access the computer system by simply talking to it. This technology is yet to come to mainstream as it is still in process of development. To date, most speech systems are used for text dictation or for single command voice menu options.
(iii) Voice Synthesizers: These are also known as voice output devices or audioresponse units. These convert data in main storage to vocalized sounds understandable to humans. They can be relatively expensive and connect to almost every computer multimedia systems, which incorporate multi-media presentation and voice output, are popular amongst consumers. Available in various uses, such as children education software, voice output serves as an excellent media for communicating information and especially for blind people. It seems from the present trends that voice output will soon become one of the dominant methods of output.
(iv) Natural Language: The most attractive means of entering data into the computer could be by natural language. Those unable to remember a command or lost in hierarchy of menus, may long for a computer which is able to understand instructions expressed in everyday words. However, due to the ambiguity of natural language (i.e., sentence structure and meaning), it is difficult for the computer to understand and execute instructions accurately. Therefore it is unlikely that such an interface would be available for sometime. Though research is continuing in this direction.
14. (a) Network Topology: The geometric arrangement of computer resources, remote devices and communication facilities is known as network structure or network topology. A computer network is comprised of nodes and links. A node is the end point of any branch in a computer whereas a link is a communication path between two nodes.
A network structure determines which elements in a computer network can communicate with each other. Four basic network structures are commonly used.
(i) Star Network: This is most common structure characterized by communication channels emanating from centralized computer system. The processing nodes interconnect directly with a central computer system. Each node can communicate only with the central server and not with other nodes in the network. If it is desired to transmit information from one node to another, it can be done only by sending the details to the central computer, which in turn sends them to the destination.
A star network is particularly appropriate for those organisations which require a centralized data base or a centralized processing facility. For example, a star network may be used in banking for centralized record keeping in an on-line branch office environment. Features of a star network are:
It is easy to add or remove nodes.
A node failure does not bring down the entire network.
It is easier to diagnose network problems through a central hub, however central hub is a critical element and its failure may bring down the entire network.
It costs more to cable a star configuration than other topologies.
(ii) Bus Network: This structure is very popular for local area networks. In this structure, a single network cable runs in the building and all nodes are linked along with this communication line with two end points called the bus or backbone. Two ends of the cable are terminated with terminators.
This structure is easy to use and understand and also reliable where network is small.
It requires least amount of cable to connect the computers together and therefore less expensive.
It is easy to extend by joining cable with connector or repeater.
Heavy network traffic can slow a bus considerably. Since any computer can transmit data any time, computers interrupting each other can use a lot of bandwidth.
Trouble shooting is difficult. A cable break or malfunctioning computer is difficult to detect, hence it can cause the whole network to stop functioning.
(iii) Ring Network: In this network structure the network cable passes from one node to another until all nodes are connected in the form of a loop or ring. There is direct point-to-point link between two neighboring nodes. These links are unidirectional which ensures that transmission by a node traverse the whole ring and comes back to the node which made the transmission.
It offers high performance for a small number of workstations or for larger networks where each station has a similar workload.
Network can span longer distances than other types of networks.
It is easily extendable.
It is relatively expensive and difficult to install.
Failure of one node can affect the entire network.
Trouble shooting is difficult.
Addition or removal of node can disrupt the entire network.
(iv) Mesh Network: In this network structure, there is random connection of nodes using communication links. In real life, network connections are not made randomly. Network lines are expensive to install and maintain. This network may be fully connected or connected with only partial links. In fully inter connected topology, each node is connected by a dedicated point to point link to every node. This means that
there is no need for any routing function. The reliability is very high. However, fully connected networks are not very common because of the high cost, only military installations, which need high degree of redundancy may have such networks. In partially connected mesh topology, computer nodes are widely scattered. The function of routing information from one node to another is done using routing protocols.
Mesh Network problems are easier to diagnose.
Yields greatest amount of redundancy in the event that one of the nodes fails where network traffic can be redirected to another node.
The cost of installation and maintenance is high.
(b) Computer network is a collection of computers and technical devices connected together by a communication system. A local area network (LAN) is primarily a data transmission system intended to link computers and associated devices within a restricted geographical area such as an office building or several adjacent buildings. The linked computers and related equipments may be anything from full-scale mainframe computing systems to small desktop office workstations, terminals and peripherals etc. The key characteristic of a local area network is the fact that the whole of the network, confined to one site, is completely under the control of one organization. Organizations use LANs because they enable multiple users to share software, data and devices. LANs use a shared physical media, which is routed in the whole campus to connect various systems. LAN uses high-speed media (1Mbps to 30 Mbps or more) and are mostly privately owned and operated.
Local area network has following five components:
(i) File Server: A network file server is a computer system used for the purpose of managing the file system, servicing the network printers, handling network communications, and other functions. A server may be dedicated in which case all of its processing power is allocated to network functions, or it may be non-dedicated which means that a part of the servers functions may be allocated as a workstation or DOS-based system.
(ii) The network operating system: It is loaded into the server's hard disk along with the system management tools and user utilities. When the system is restarted, NetWare boots and the server comes under its control.
(iii) Workstations: Workstations are attached to the server through the network interface card and the cabling. Workstations are normally intelligent systems, such as the IBM PC. The concept of distributed processing relies on the fact that personal computers attached to the networks perform their own processing after loading programs and data from the server. Hence, a workstation is called an Active Device on the network. After processing, files are stored back on the server where they can be used by other workstations.
(iv) Network interface card: Every device connected to a LAN needs a Network
interface card (NIC) to plug into the LAN. For example, a PC may have an Ethernet card installed in it to connect to an Ethernet LAN.
(v) Network Cabling: Once the server, workstations and network interface cards are in place, network cabling is used to connect everything together. The most popular type of network cable is the shielded twisted-pair, co-axial and fiber optic cabling.
15. (a) The Internet is a global network of computer networks that was initiated in the year 1960's by a team of scientists under a U.S. Government contract. There are approximately 1,40,000 small networks in more than 200 countries connected through Internet. These networks are formed by various educational, commercial, Government, non-profit and military organizations. These networks are individually owned and operated that are all interconnected.
Internet is a combination of number of computers, linked together, sharing same resources. There are thousands of databases containing information of all sorts in addition to the facilities like e-mail, chatting, games, message boards and free software.
Networks comprise addressable devices or nodes (computers) connected by communication channels. Any node can transmit a message to any other node, along with communication channels, via the intermediate nodes.
Information on the business and services is placed in an assembled fashion in a common location.
Access to this information is provided at reasonable costs (which are steadily declining, and with a significant reduction in duplication and distribution costs).
A mechanism for immediate feedback from consumers or business partners is provided.
The cost of information delivery to internal and external sources is reduced.
Employee access to significant amounts of information is increased.
An efficient means of updating and disseminating current information to customers and internal staff is provided.
Customized information to consumers is delivered (for example, individual investment portfolios can be tracked).
(b) Electronic commerce is the process of doing business electronically. It involves the automation of a variety of business-to-business and business-to-consumer transactions through reliable and secure connections.
EC-related literature revealed the following definitions of EC:
Electronic Commerce is a composite of technologies, processes and business strategies that foster the instant exchange of information within and between organizations. EC strengthens relationships with buyers, makes it easier to attract
new customers, improves (and in some cases reinvents) customer responsiveness, and opens new markets on a global scale.
Electronic Commerce is the application of various communications technologies to provide the automated exchange of business information with internal and external customers, suppliers and financial institutions. Examples of these technologies include Electronic Data Interchange (EDI), bar coding, scanning, E-mail and fax, to name a few. The bottom line is that Electronic Commerce requires a paradigm shift in the way corporations do business today.
There are three distinct general classes of e-commerce applications:
Customer to business: Customer to business e-commerce applications include:
Social portals: Electronic applications enable consumers to find online information about existing and new products and services. This also includes applications that enable consumers to communicate with each other through electronic mail, video-conferencing, and newsgroups.
Transaction portals: These include applications that enable and facilitate the completion of transactions between buyers and sellers. In electronically facilitated consumer-to-business transactions, customers learn about products through electronic publishing, buy products with electronic cash and other secure payment systems, and even have information goods delivered over the network.
(ii) Intra-organisation applications: Intra-organisational e-commerce applications include:
Workgroup communications: These applications enable managers to communicate with employees using electronic mail, videoconferencing, and bulletin boards. The goal is to use technology to increase the dissemination of information, resulting in better-informed employees.
Collaborative publishing: These applications enable companies to organise, publish, and disseminate human resources manuals, product specifications, and meeting minutes using tools such as the World Wide Web. The goal is to provide the information to enable better strategic and tactical decision making throughout the firm. Also, online publishing shows immediate and clear benefits: reduced costs for printing and distributing documentation, faster delivery of information, and reduction of outdated information.
Sales force productivity: These applications improve the flow of information between the production and sales forces, and between firms and customers. By better integrating the sales forces with other parts of the organisation, companies can have greater access to market
intelligence and competitor information, which can be funneled into better strategy. The goal is to allow firms to collect market intelligence quickly and to analyze it more thoroughly.
(iii) Inter-organisation Applications: Inter-organisational e-commerce applications
include:
Supplier management: Electronic applications help companies reduce the number of suppliers and facilitate business partnerships by reducing purchase order (PO) processing costs and cycle times, and by increasing the number of POs processed with fewer people.
Inventory management: Electronic applications shorten the order-ship-bill cycle. If the majority of a business's partners are electronically linked, information once sent by fax or mail can now be instantly transmitted. Businesses can also track their documents to ensure that they were received there by improving auditing capabilities. This also helps to reduce inventory levels, improve inventory turns, and eliminate out-ofstock occurrences.
Distribution management: Electronic applications facilitate the transmission of shipping documents such as bills of lading, purchase orders, advanced ship notices, and claims, and enable better resource management by ensuring that the documents themselves contain more accurate data.
Channel management: Electronic applications quickly disseminate information about changing operational conditions to trading partners. Technical, product, and pricing information that once required repeated telephone calls and countless hours can now be posted to electronic bulletin boards. By electronically linking production-related information with international distributor and reseller networks, companies can eliminate thousands of hours of labour and ensure accurate information sharing.
16 (a) Following five areas of DBMS managements are be considered when trying to
maintain a well-tuned database:
Correct installation of the DBMS product.
Ensuring that adequate file space is available.
Proper allocation of disc space for database.
Allocation of data files in standard sizes for I/O balancing.
(ii) Memory Usage - One should know about following memory management issues:
How the DBMS uses main memory ?
What needs the programs in main memory have?
Knowledge of above issues can help in efficient usage of memory.
(iii) Input / Output (I/O) contention
Achieving maximum I/O performance is one of the most important aspects of tuning. Understanding how data are accessed by end-users is critical to I/O contention.
Simultaneous or separate use of input and / or output devices.
Clock speed of CPU requires more time management of I/O.
Spooling/Buffering etc. can be used.
Knowledge of how many and how frequently data are accessed, concurrently used database objects need to be striped across disks to reduce I/O contention.
Multi programming and multi processing improve performance in query processing Monitoring CPU load.
Mixture of online/back ground processing need to be adjusted.
Mark jobs that can be processed in run off period to unload the machine during peak working hours.
(b) Data Volume and Usage Analysis: Data-volume and usage analysis i.e. frequency-of-use statistics are critical inputs to the physical database design process. The volume and frequency statistics are generated during the systems analysis phase of the systems development process when systems analysts are studying current and proposed data processing and business activities. The data-volume statistics represent the size of the business, and should be calculated assuming business growth over at least a several-year period. The access frequencies are estimated from the timing of events, transaction volumes, and reporting and querying activities. Since many databases support ad hoc accesses, and such accesses may change significantly over time, the access frequencies tend to be less certain than the volume statistics. Fortunately, precise numbers are not necessary. What is crucial is the relative size of the numbers, which will suggest where the greatest attention needs to be given in order to achieve the best possible performance. Data volume and usage analysis helps in taking decisions regarding the following:
Hardware configuration including Processor speed and Hard disk capacity
File organization and Indexing field
Selection of a database structure like Hierarchical, Network or Relational database structure
Selection of DBMS/RDBMS like Foxpro, MS-Access, Oracle or SOL.
Computer Crimes and Penalty in IT Act 2000: In IT Act, 2000, the Chapter XI deals with some computer crimes and provides penalties amounting one to two years imprisonment with or without a fine of 1-2 lakh or both. The Section 65 to 78 deals with these crimes and provides for penalties for these offences. Some of the important crimes are as following:
(i) Section 65 provides for punishment for tampering with computer source documents
(ii) Section 66 provides for punishment for hacking with computer system
(iii) Section 67 provides for punishment for publishing or transmitting or causing to be published or transmitted, information which is obscene in electronic form.
Power of the Controller
(i) Section 68 provides that the Controller may give directions to a Certifying Authority or any employee of such authority to take such measures or cease carrying on such activities as specified in the order, so as to ensure compliance with this law. If any person fails to comply, he shall be liable to imprisonment upto 3 years or five upto Rs. 2 lakhs, or both.
(ii) Section 69 empowers the Controller, if he is satisfied that it is necessary or expedient so to do in the interest of sovereignty and integrity of India, security of the State, friendly relation with foreign states or public order, to intercept any information transmitted through any computer system or computer network.
(iii) Section 70 empowers the appropriate Government to declare by notification any computer, computer system or computer network to be a protected system. Any unauthorised access of such systems will be punishable with imprisonment which may extend to ten years or with fine.
Section 71 to 78 of IT Act provides for penalties.
(b) Objectives of the Information Technology Act, 2000
(a) To grant legal recognition to transactions carried out by means of EDI and E-Commerce in place of paper based methods of communication.
(b) To give legal recognition to digital signatures for authentication of any information.
(c) To facilitate electronic filing of documents with Government Departments.
(d) To facilitate electronic storage of data.
(e) To facilitate and give the legal recognition to electronic fund transfers between bank and financial institutions.
(f) To give legal recognition for keeping books of accounts in electronic form by bankers.
(g) To amend the Indian Penal Code, the Indian Evidence Act, the Banker's Book Evidence Act and Reserve Bank of India Act.
18. (a) Benefits of Flowcharts
The benefits of flowcharts are elucidated below :-
(i) Quicker grasp of relationships - Before any application can be solved, it must be understood, the relationship between various elements of the application must be identified. The programmer can chart a lengthy procedure more easily with the help of a flowchart than by describing it by means of written notes.
(ii) Effective Analysis - The flowchart becomes a blue print of a system that can be broken down into detailed parts for study. Problems may be identified and new approaches may be suggested by flowcharts.
(iii) Communication - Flowcharts aid in communicating the facts of a business problem to those whose skills are needed for arriving at the solution.
(iv) Documentation - Flowcharts serve as a good documentation which aid greatly in future program conversions. In the event of staff changes, they serve as training function by helping new employees in understanding the existing programs.
(v) Efficient coding - Flowcharts act as a guide during the system analysis and program preparation phase. Instructions coded in a programming language may be checked against the flowchart to ensure that no steps are omitted.
(vi) Orderly check out of problem - Flowcharts serve as an important tool during program debugging. They help in detecting, locating and removing mistakes.
(vii) Efficient program maintenance - The maintenance of operating programs is facilitated by flowcharts. The charts help the programmer to concentrate attention on that part of the information flow which is to be modified.
The limitations of flowcharts are as given below :
(i) Complex logic - Flowchart becomes complex and clumsy where the problem logic is complex.
(ii) Modification - If modifications to a flowchart are required, it may require complete redrawing.
(iii) Reproduction - Reproduction of flowcharts is often a problem because the symbols used in flowcharts cannot be typed.
(iv) Link between conditions and actions - Sometimes it becomes difficult to establish the linkage between various conditions and the actions to be taken there upon for a particular condition.
(v) Standardisation - Program flowcharts, although easy to follow, are not such a natural way of expressing procedures as writing in English, nor are they easily translated into Programming lauguage.
(vi) The essentials of what is done can easily be lost in the technical details of how it is done.
(vii) There are no obvious mechanisms for progressing from one level of design to the next e.g., from system flowchart to run flowcharts, program flowchart etc.
|
(b) Flow Chart |
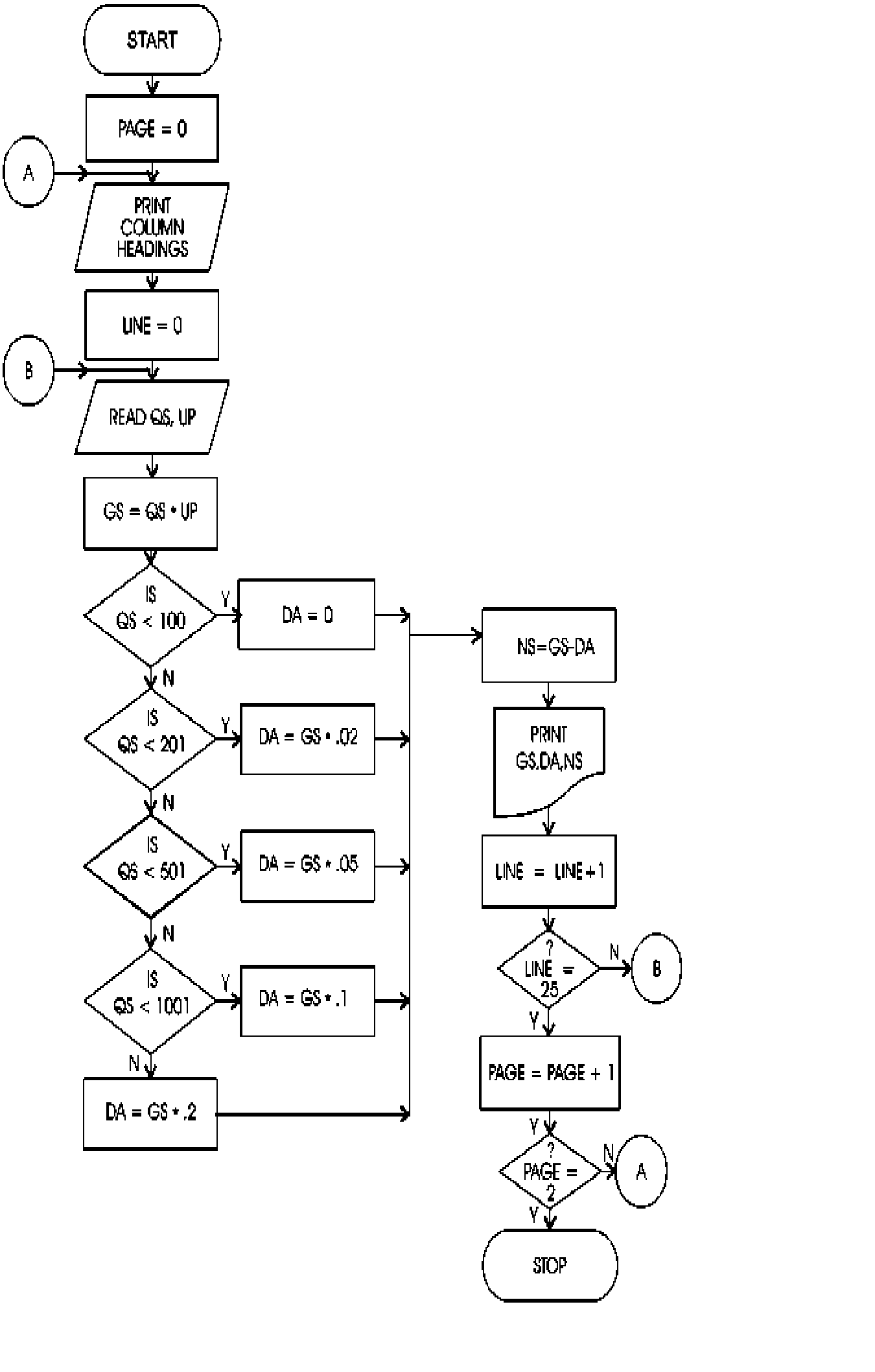 |
19. (a) Types of Decision Table
There are three types of decision table :
Limited Entry Tables - In a limited entry table the condition and action statements are complete. The condition and action entries merely define whether or not a condition exists or an action should be taken. The symbols used in the condition entries are :
Y: Yes, the condition exists N: No, the condition does not exist.
: Irrelevant, the condition does not apply, or it (or blank) makes no difference whether the condition exists or not.
The symbols used in the action entries are:
X : Execute the action specified by the (or blank) action statement.
: Do not execute the action specified by the (or blank) action statement.
Extended Entry Table : The condition and action statements in an extended entry table are not complete, but are completed by the condition and action entries.
Example:
|
Granting Credit Facility |
R1 |
R2 |
R3 |
|
C1 |
Credit Limit |
OK |
Not OK Not OK |
|
C2 |
Pay Experience |
- |
Favourabl Unfavourable |
|
A1 |
Credit Facility |
Allow |
Allow - |
|
A2 |
Credit Action |
- |
- Reject Order |
Mixed Entry Table : The third type of decision table is the mixed entry form which combines both the limited and extended entry forms. While the limited and extended entry forms can be mixed within a table, only one form may be used within a condition statement/entry or an action statement/entry.
|
Example : | ||||||||||||||||||||
|
|
Conditions |
1. |
Rules 2. 3. Condition entries |
4. |
|
Sales region code >= 10. |
Y |
YN |
N |
|
Invoice amount Rs. >= 10,000 |
Y |
NY |
N |
|
Action Stub |
Action entry | ||
|
Delivery charges | |||
|
Add Rs. 100 to invoice total |
X | ||
|
Add Rs. 150 to invoice total |
X | ||
|
Add Rs. 200 to invoice total |
X | ||
|
Add Rs. 250 to invoice total |
X |
20. (a) Mail Merge is a tool for producing repetitive documents. It gives flexibility while sending letter and then personalizing each copy of it with information such as names, addresses, dates etc. For establishing Mail Merge, two documents need to be created, i.e. the main document and the data source. Following steps are followed to set-up Mail Merge:
(i) Setting up the Main Document.
(ii) Setting up the Data Source.
(iii) Editing the Data Source.
(iv) Addition of fields to the Main Document.
- Place the cursor in the Main Document where we want our first field to appear.
- Activate the Insert Merge Field' button from the Mail Merge toolbar.
- From the list, select the field that we would like to place first.
- Take the cursor to the next line.
- Click the Insert Merge Field' and select the next field. Continue doing this until we get all the required fields on our main document.
(b) Working With Tables
Table is simply the arrangement of information in rows and columns.
(i) Creating Tables: There are several ways to insert tables in a document.
Using the Insert Table button
Using the Table/Insert Table option
Using the Table/Convert Text to Table option
Using Draw Table' Tool
(iii) Deleting rows and Columns
(iv) Resizing Rows and Columns
For more details of the above points, students are advised to refer to the study material Chapter-16.5
21. (a) Concept of MACRO in MS-EXCEL: Macro is a small program that carries out predefined and pre-recorded series of steps by giving a few keyboard shortcuts. It is like a recorded movie which can be run any number of times. It automates tasks, thus saves a lot of precious time. EXCEL offers macros in two languages - Excel Visual Basic and Excel 4.0 Macro language. In Excel 4.0 macro language, a macro can be created by following the procedure explained below:
Steps for creating a new Macro on MS-EXCEL: Before proceeding to create a macro in MS-Excel, first decide the steps that are supposed to be performed by the macro. Following steps are then carried out:
(i) Select Tools/Macro' option from the main menu.
(ii) Select Record new Macro' option from the cascading menu.
(iii) Name the macro under which it is to be saved. A macro can be assigned a name in the Macro name' box.
(iv) The user can assign a keyboard shortcut to the macro. It will enable him to execute the macro using a keyboard.
(v) In case the macro is to be used in the current work book only, then in Store Macro in' box, select the option This workbook' from the drop down list. However, if the macro is to be made available to other workbooks also, then New workbook' option may be selected from the drop down list. Excel will ask the name of the new workbook in which the macro is to be saved.
(vi) In the Description' box, give some relevant and important details about the macro such as purpose, date of creation and owner of macro etc.
(vii) Once all relevant details are filled in the Record Macro' box, click at the O.K' button.
(viii) Perform all the essential steps required to accomplish the desired task. Now click at the stop recording' button on the Stop Recording' toolbar.
(ix) The macro is now ready to be executed.
(b) (i) FV: It is a financial function, which calculates the future value for a series of equal investments (also called annuity) earning a fixed periodic rate of interest.
(ii) INT( ): It is a mathematical function which rounds a number down to the nearest integer.
Syntax of the function is:
INT (number) where,
number' is the real number you want to round down to an integer.
(iii) COUNTIF( ): It is a statistical function which counts the number of cells within a range that meet the given criteria.
Syntax of the function is:
COUNTIF(range, criteria)
where,
range' is the range of cells from which you want to count cells.
criteria' is the criteria in the form of a number, expression, cell reference, or text that defines which cells will be counted.
(iv) ABS(X): It is a mathematical function used to calculate the absolute value of x where x is any number. For example, if x = -3 then ABS (x) = 3.
(v) SUM (numberl, number2, ....): It is a mathematical function, which calculates the sum of all the numbers in a range of cells.
(vi) LEN (text string): It returns the number of characters in the text string e.g. if text string = Examination', then this function will return 11.
(vii) PROPER (text string): This is a text function which capitalizes the first letter in each word of a text string and converts all other letters to lowercase letters, e.g. if the text string is 'eXAMination', then this function will return 'Examination'.
(viii) UPPER (text string): This text function converts a text string to all uppercase letters e.g. if the text string is exam', then this function will return EXAM'.
(ix) DMAX: It is a data base function, which returns the largest number in the field of records in the database that matches the conditions you specify.
(x) CLEAN ( ): It is a text function which removes all nonprintable characters from text.
Syntax of the function is:
CLEAN(text)
where,
text' is any worksheet information from which you want to remove nonprintable characters.
22. (a) Power point comes with different views to help in creating better presentations. It offers five views:
(ii) Outline View (iii) Slide View
(i) Normal View (iv) Slide sorter View
(v) Slide show View.
Each view offers a different way to look at the presentation and modify it. One can
easily switch between the various views using the buttons on the left hand corner of
the scroll bar.
(i) Normal View: Normal view is a tri-pane view which offers the slide view, the outline view and the Notes pane. The user should work in normal view when there is a need to frequently switch between text and objects on slide. This view allows editing text both on the slide and the outline view. The slide is also large enough for inserting objects.
(ii) Outline View: It is the most comfortable view for working on text. The standard and formatting toolbars are available for editing text. The user can therefore work on the text just like MS- WORD. One can even check spellings and use Find and Replace features to modify text. In this view, the slide is visible only in miniature form. Notes can also be added.
(iii) Slide View: The slide view allows the user to see how the text and objects that have been created will appear on each slide. In this slide view, it is convenient to insert objects and modify them. Sometimes, the text inserted on a slide using outline view, runs into too many lines on the slide and even runs out of the slide. In such cases, it is required to trim the text or use an additional slide. The user can edit the text on each slide in the slide view.
(iv) Slide Sorter View: It is possible to view all the slides at one time in the slide sorter view. Though it is not possible to rearrange the text or objects on individual slides in this view but one can move the slides around. Even in outline view the slides can be moved around. But if it is desired to see the visual effect of the rearrangement, then the slide sorter view is most useful.
(v) Slide Show View: This view displays slides in a sequence, moving from one slide to another, transitioning with special effects that have been set, and moving at a preset timings that can be controlled.
(i) Working with the text in a slide: It is important that the text and the objects on the slides are arranged well for the best visual impact.
Arranging Text in Different Levels : While adding text to the slides, the contents are presented in short and compact language. To increase clarity and precision of the presentation, the lines are bulleted. The text can be arranged in several levels of importance. Below the Title text it is possible to introduce five levels.In PowerPoint 2000, the text font appears the same size in each level, PowerPoint has an AutoFit feature that adjusts all the text placed in the Outline view of a slide on a Slide by changing the font size according to the level occupied by each line of text. This will ensure that no text runs of the bottom of the slide in Slide view. However, sometimes the text is adjusted so much that the readability of text suffers. The AutoFit feature can be disabled.
The bullets of the different levels of text in the Outline have a different size and shape. To move a line up or down the different levels, the Tab can be used. To move a line one level below the previous line, the tab should be pressed once. To promote a line one level up, Shift and Tab ought to be pressed.
(ii) Work With The Slide Master: It is possible to change the design of the slide layout and format the text on each slide using the slide master.The slide masters also hold the background items for each slide. The changes made to a Slide master are reflected on each slide of the presentation. individual slide can be modify to look different, the changes can be made on the slide itself, without changing the master.
The Slide master controls the format and placement of titles, text and graphic objects on slides. Some presentations have two Slide master for a presentation. Sometimes the title has a different design. Then a separate Title master determines the format of text and design of the title slide.The Slide master can be accessed from the Views menu, Master option.
23. (a) The use of computer-assisted audit techniques (CAAT) in a organization primarily
depends upon the following factors:
(i) Computer knowledge, expertise and experience of the auditor: The auditor should have sufficient knowledge to plan, execute and use the results of the particular CAAT adopted. The level of knowledge required depends upon the complexity and nature of the CAAT and of the entity's accounting system.
(ii) Availability of CAATs and suitable computer facilities: The auditor should consider the availability of CAATs, suitable computer facilities and the necessary computer-based accounting systems and files. The auditor may plan to use other computer facilities when the use of CAATs on the entity's computer is uneconomical or impractical.
(iii) Impracticability of manual tests: Many computerized accounting systems perform tasks for which no visible evidence is available and, in these circumstances, it may be impracticable for the auditor to perform tests manually. The lack of visible evidence may occur at different stages in the accounting process. For example, where orders are entered online, input documents may be non existent. The system may not produce a audit trail of transactions processed through the computer. Output reports may either be not printed or a printed report may contain only summary totals.
(iv) Effectiveness and Efficiency: The effectiveness and efficiency of auditing procedures may be improved throughout the use of CAATs in obtaining and evaluating audit evidence. The auditor may consider the life cycle of the CAAT application in the evaluation of the efficiency and effectiveness of a CAAT.
(v) Timing: Certain computer files, such as transaction files, are often retained only for a short time and may not be available in machine readable form when required by the auditor. Thus, the auditor will need to make arrangements for the retention of data.
Where the time available to perform an audit is limited, the auditor may plan to use a CAAT, as it will meet his time requirement better than other procedures.
(b) Integrated Test Facility - ITF is a particular form of test data involving the establishment of a dummy entity through which data may be procured. Once the dummy entity is established, the auditor can input transactions and process these using the clients live system alongside the client's live data. It will be necessary to delete the test transactions from the system after the test has been performed. As with all test packs, the output produced is compared with predicted results to determine whether the programmed procedures being tested are operating correctly.
An ITF can be particularly useful in more complex environments, for example, in an on-line, real time banking system. A single terminal can be set up as an "audit bank" (a separate branch which is not consolidated into bank's accounts), which can then be used to perform any of the banking functions for its own dummy customers. In this way extensive testing of the entire system may be carried out without the client's staff being aware that it is taking place.
In order for the ITF technique to be effective the auditor should have a detailed knowledge of the complete system, including the possible effects of the ITF data on all related system files. Knowledge amongst the client's staff of the existence of the Integrated Test Facility should be limited to those who need this knowledge in order to perform their tasks properly.
24. (a) Facilities provided by Financial Accounting Package
Financial accounting package must be user friendly with on-line help facility so that even novice user can use it without any problem. Security must be of prime importance in a good financial accounting package so that no unauthorized user can enter/modify the financial data. It must provide the following facilities:-
a. It must offer well designed data entry screens with various verification/validations controls so that correct data could be entered easily and fastly.
b. It must have screen to create information about company such as its name, address, contract numbers, Income tax number, Sales tax number and other relevant details
c. It must have flexibility to modify the company's accounting and inventory features by the authorized users using their passwords.
d. It must be able to maintain the Group Accounts (Single Group & Multiple Groups) as well as single and multiple ledgers.
e. It must facilitate day-to-day accounting transactions through voucher entry like entry of sales, purchase, receipt, payment and journal vouchers without the need of remembering the accounting codes.
f. It must generate various financial statements like Day book, Cash book, Bank book, General ledger, Subsidiary ledger, Profit & Loss A/Cs, Trial balance, Balance sheet
etc. In addition to these, the package must prepare various financial statements required by auditors and Government. It must be possible that all the required reports could be customized by user according to their requirements rather than generation of the same in standardized formats.
(b) (i) Purchase Entry
Step 1: In Voucher Creation press the F9 function key on the keyboard to begin Purchase entries.
Step 2: Press the F2 function key on the keyboard to enter the purchase entry date as 1-Jan-2010.
Step 3: Skip the reference field by pressing the Enter key.
Step 4: In the Particulars column to give the Cr effect: Type the alphabet H and select Hyundai from the List of Ledger Accounts displayed on the right hand side of the screen and press Enter.
Step 5: In the Credit column, type the Total Price as Rs. 5000000/- and press Enter.
Step 6: In the next line, to give the Dr effect: Type the alphabet P and select Pur Santro from the List of Ledger Accounts displayed on the right hand side of the screen and press Enter. Tally now enters the Inventory Allocation screen.
Step 7: In Inventory Allocation for Pur Santro dialogue box, for Name of the Item
type the alphabet S and select Santro from List of Items then enter Quantity as 5. The Rate and the Amount are automatically calculated. Press the Enter key to accept the dialogue box and return to the Purchase Voucher.
Step 8: The Narration can be entered if desired in the Narration field. Press Enter to Accept the purchase entry.
(ii) Sales Entry
Step 1: In Voucher Creation, press the F8 function key on the keyboard to begin Sales entries.
Step 2: Press the F2 function key on the keyboard to enter the sales entry date as 21-2010
Step 3: Skip the reference field.
Step 4: In Particulars, to give the Dr effect: Type the alphabet D and select Grindlays Bank from the List of Ledger Accounts displayed on the right side of the screen and press Enter.
Step 5: In the Debit column, type the Total Price as Rs. 350000/- and press Enter.
Step 6:To give the Cr effect: Type the alphabet S and select Sales Santro and press Enter. Notice the amount automatically appears in the Credit column. Tally now displays the screen for Inventory allocation for sales Santro.
Step 7: In the Inventory Allocation for sales Santro dialogue box type, in the Name of the Item, column type the alphabet S and select Santro from the List of Items and press Enter. Type the Quantity 1 and press Enter. Notice the Rate and the Amount appear automatically. Press Enter to accept the dialogue box and return to the Sales voucher.
Step 8: The Narration can be entered if desired in the Narration field. Press Enter to accept the sales entry.
25. (i) Bar Code Reader: It is the most commonly used input device in supermarkets and departmental stores. This device converts the bar code which is a pattern of printed bars on products, into a product code by emitting a laser beam which reflects off the bar code image. A light sensitive detector identifies the bar code image by recognizing special bars at both ends of the image. Once the detector has identified the bar code, it converts the individual bar patterns into numeric digits and feeds that number to the computer, just as though the number had been typed on a key board.The special bars at each end of the image are different, so the reader can tell whether the bar code has been read right side up or upside down. After the bar code reader has converted a bar code image into a number, it feeds that number to the computer for further processing.
Bar code reader provides following advantages:
- improves accuracy of data entry
- better customer service
- faster check out at the point of sale
- greater control and reliability of inventory records
- most widely used input device after the keyboard and mouse.
Bar code readers are also used in industries that must count and track inventory, such as retail, medical libraries, military and other government operations.
(ii) Smart Card Systems: Smart cards are similar to credit card in size and shape but have small microprocessor chip and memory to store the details of the card holder.
So far, smart cards are used mostly for E-commerce and EFT (Electronic fund transfer). However, these days smart cards are being used to store the complete details of the card holder such as holders particulars, identity, address, insurance data, relatives' details, medical background and even finger prints of the holders. These cards can help the doctors to provide immediate treatment in case the cardholder is disabled by an accident or illness. It can serve as an identity card at various security checkpoints, the stored fingerprints could be compared to fingerprints of people who are authorized to enter a secured area.
Data from Smart cards is read with the help of a device known as Smart Card Reader. Smart cards are going to replace the need of multiple documents to be
retained by a person like Ration card, Driving license, Passport, Identity card, Voter card etc.
(iii) Diagnostic Routines: It is a system software which is usually a part of operating system and is provided by the computer manufacturer. These are those programs which help the user in debugging of program as well as to find out the details of various equipments used in the computer, like:
1. What type of Processor is installed in the computer like P-III or P-IV and its speed?
2. What is total amount of main memory like 128MB/256MB?
3. What type of keyboard is attached with the computer like 101 Keys/104 keys/Multimedia Keyboard?
4. What is display type like VGA/SVGA?
5. What type of mouse is attached with computer like 2 buttons/3buttons/scroll mouse/Mechanical Mouse/Optical Mouse?
6. Is separate math coprocessor present in computer?
7. Where is BIOS (Basic I/O) manufacture like AWARD BIOS or ANI BIOS?
(iv) Wireless Networks: People on the road often want to use their portable computers like Laptop or Notebook computers to send and receive electronic mails, read remote files from the server of their office and to surf the Internet from anywhere on land, sea or air. Since a wired network is impossible in cars and aeroplanes, hence it resulted in the development of wireless network. WAP (Wireless Application Protocol) is the protocol used in Wireless communication. Laptop computers with wireless card are available in the market. Wireless technology known as Bluetooth allows the user to transfer the data between computer and Mobile Phone/Digital Camera. Airports and some Indian Universities have been converted to Wireless fidelity (Wi-Fi) zones which are allowing users to use Internet services anywhere within the premises of Airport.
Wireless networks are of great use for those persons who remain away from their home/office for most of the time. Another use of wireless network is for the rescue workers at the disaster sites like fires, floods or earthquake sites where telephone system gets destroyed.
(v) Digital Signature: Digital signature is a form of security for electronic records that the dual key technology offers. The digital signature is encrypted with a private key which when attached to an encrypted message uniquely identifies the sender. Since the encryption used in the digital signature is linked to the message sent, forger' will be unable to copy the digital signature by simply cutting and pasting it to another message. Section 3 of Information Technology Act gives legal recognition to electronic records and digital signatures.
The digital signature is created in two distinct steps. First, the electronic record is converted into a message digest by using a mathematical function known as "hash function which digitally freezes the electronic record thus ensuring the integrity of the content of the intended communication contained in the electronic record. Any tampering with the contents of the electronic record will immediately invalidate the digital signature. Secondly, the identity of the person affixing the digital signature is authenticated through the use of a private key which attaches itself to the message digest and which can be verified by anybody who has the public key corresponding to such private key. This will enable anybody to verify whether the electronic record is retained intact or has been tampered with since it was so fixed with the digital signature. It will also enable a person who has a public key to identify the originator of the message.
(vi) Webcasting or push technology is web-based technology. This allows users to passively receive broadcast information rather than actively search the Web for information. Push technology allows users to choose from a menu of sources, specifying what kind of information they want to receive. Once selected, the information is automatically forwarded to the user. Internet news services, which deliver the day's activities to the user's desktop, are an example of push technology.
Users can also download software, select the frequency with which they will receive services, and subscribe to a variety of information sources. There is very little cost involved to the user for push services because information is delivered with advertising, and users view their custom-tailored news off-line. Webcasting eliminates the frustration of the user which he/she faces while surfing the Internet to get right kind of information.
133
bits.
|
Attachment: |
| Earning: Approval pending. |
