Jadavpur University 2010 M.E Software Engineering Principles of in - Question Paper
Jadavpur University
M.E in Software Engineering
1st Semester Examination, 2010
Subject:Principles of Software Engineering
TIME: 3 Hour*
EX/PG/SWE/r/112A/139/2011
ME Software Engg I* Semester Examination. 2011 Principles of Software Engineering
FULL MARKS: 100Answer Any FIVE Questions
Guidelines for the Esaminee:*
I Always start a new queatton ta fresh paga
t While answering a question, please wrtta ih eompteic number like, la,
2c,4detc
3. Prectse and lo-thepomt aMwer will he rewarrterl
4. legible handwriting and clean drawing will be rewarded
5. Answering more than 5 question* will be penalized
l a) Describe how Software Engineering stands apart from System Eofsaccnng and Computer Scicnce*
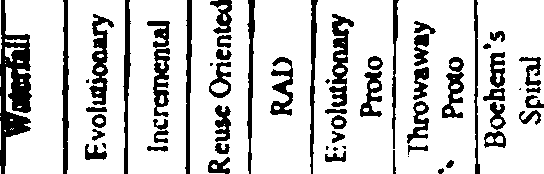
b) Considering the fact that there are quite a few Software Process ModeH, one has to apply certain logistics regarding choosing a particular process model over the others for different kind of customer/vendor situations. The following table tries to capture these scenarios.
In this table, the 2* column from the left describes different types of customerAndor situations. There are altogether 15 such situations. Please go through all these situations and apply your own logistics regarding choosing a particular process model which will be appropriate to develop the software product taking care of that particular situations. Please mark the corresponding entry under the correct process model column.
f
Different Customer/Vendor Situation
The customer U not in a hurry. They are very much well aware about (heir
requirement They dont mind taking a v
conservative spproach towards developing the orodnct_
*tta Software needs to be deployed as soon as possib!e_
The Customer is very cautious about taking wrong steps. They need to assess
_fiaksaftcr every ccjc ____
The Customer wants to get look nd fee! bout the product which they will get at the end of the rood They dont mind pending tome little money now, so that they can get tome idea about the product
__up front
The timation hens also U the same as above, but customer feels that their initial little investment *hould be protected as much as possible The customer has enough money am) time. The vendor also has enough man power. Both the parties are well aware of the requirements____
The Vendor does not have sufficient manpower And the customer does not Iwwanfc hariot itng Inn B&m receMnflthe final1 . time is of great tmportancorthe customer. The customer does not mind iF the vendor uses off-the-shelf components for developing the product. The customer is also ready to tweak the requirements for this purpose if accessary
Getting (he product idea upfront b a priority for the customer. They (customer) don't mind spending some extra money at the beginning, so that they are not in the dark about the look and feel of the final
9.
The customer does not have much idea regarding the behavior of the end product, and to ts the vendor. So customer is ready
lo take it ts it goes on and the product gets
bit faf bit
The customer docs not want to wait till to the end to receive the final product; rather ***** iMcrrocdiate version of the product which they will use to train their cmalff
|
1 1 tz |
~r The customer does not mind using the J modules and components from the older 1 version of the product | ||||||||
|
13. M. |
As far as customer is concerned, assessing risk at every phase of the software development life cycle is a priority | ||||||||
|
The customer is very much comfortable toward* the incremental development approach when it cornea about developing ihegfadM. | |||||||||
|
15. |
The customer wants to have the product within next 75 days They don't mind if MnM teams work to develop the product |
2. Draw the ERD and DFP (level 0 and level I only) Tor (he fettowwg pcnMcin amk>. prcptrc the Data Dictionary for the same problem (7*t<$)
The department of public works for a large city has decided lo develop Weivbesed Pothole Tracking and Repair System (PTRS). Citizens cat log oc*> a Website and report the location (street name, number and on which portion of the street the pothole lies, e-g., middle cubs etc.) and seventy (in a scale of I to 10, depending upon the size of the pothole). Citizens also log there name, address and phone number*. Every such report are stored with an Pothole Identifying Number (PIN). This Ksl is consulted around end of the week by the Higher Administrative Authority (HAA) and assigned a repair priority number (depending upon severity and street address) for every PIN. This list can be called Pothole Occurrence List (POL).
During the beginning of every week the repair department consults the POL and prepares PTL (Pothole Tracking List). In PTL, there will be Pothole Status Information (the values of status are 'work in progress' . '% of completion*, repaired, not repaired' and 'temporary repair') and repair team number against every PIN.
At the end of the repair, the repair department also prepares Pothole Expense List (PEL), where all the expenses are recorded against every PIN. The details of expetttc may include, repair team number, number of workers involved, total hours spent at pothole repair, total materials and labor expense, calendar time used etc.
It ta to be noted that POL and PTL can he viewed by public but not PEL.
3- a) ohr BPfcrbf explanati.m about how mfonnron from the Requirement phase, is fed to Design phase
b) Fill up (he following table regarding the type of coupling (Low Coupling. Moderate Coupling. High Coupling or Highest Coupling) for the four modules (main. AA, BB and CC) mentioned below * 3)
|
mmum |
TypeofConpHw , |
PoaaJMe Explanation |
|
A* 1 | ||
|
BB 1 | ||
|
cc _ 1 ___ | ||
hit vwl, var2. v*r3,
int AA (int wl I) (
Int varl?;

return (var!2 + varl 1);
}
BB (ini v*r8, int vr9, int varlOjrtr) int varl!; Avarll-varJOjHr, v3-55 var + vw9 + var2; varl I-45;
iatCC ( u* my fl-f
rbe
I
tntvar4.varS.var6.var7.var 13. YES FLAG: f
var2 AA (var4); vw5 varl;
BB (varS. var6. Avar?),
YES FLAO-O; v*rl3-CC(YES_FLAG);
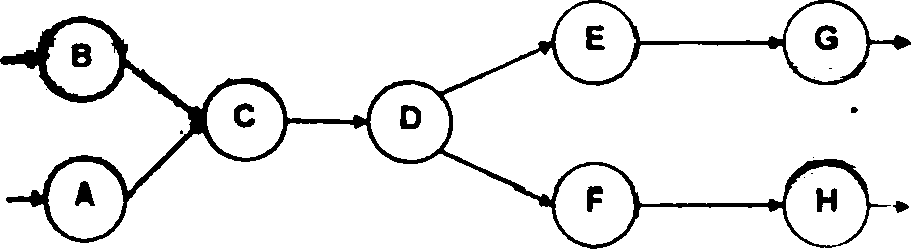
c) Map the following DFD to a suitable call and return archstec&re. Abo tty cJearty which mapping technique you are following. It is to be noted that data fkm rhanrrrriftics from C to D toE or F is quite random in nature. (4)
4. a, Ac topics Of Interface Design pke ptota wha. do undmtandhy
Users Memory Load Reduction" and Interface Consistency . ( )
a) Rcgtnwig
b) For the SafeHoroe (Home Security Monitoring System) problem, assume that the yitcm is connected to the internet via a modem. Write a decision table (with regard to the component level design) based on the following facts:-
The homeowner is supposed to get an H-Mail if and only if noise level goes beyond a certain level If the temperature of any of the rooms goes beyond a certain level (fire situation), not only homeowner will be getting an E-Mail, but also the alarm has to be switched on along with a telephone call u> a local police station. As for as pressure and vibration Is concerned (window breakage detected), when it goes beyond a certain level, alarm needs to be turned on along with a telephone call to a local police station.
(7)
e) Study the following program, fhe program has no flaw and la working alright. Try to improve the readability of the program by introducing proper mdeotttiona, comments and formatting Since, the program Is working alright, dont think about changing the logistics of the program.
int max; If (a>b) then max=a; else max=b; If (max<c) then maxc; printf ( 'The maximum number is a %<f max), }
(7)
1 a) Design test cases for White Box Testing for the following program
A program reads 3 integer values. The 3 values represent the 3 sides of a triangle. The PKV*m prints a message telling whether the triangle is scalene, isoscelcs. or equilateral.
b) Also, design lest cases for Black Box Testing for the same program mentioned above.
c) Explain whai yo understand by 'Top-down Integration Testing*
(8 * A f 6)
Jt) Explain with example what you understand by Process, Project and Product Metrics'*.
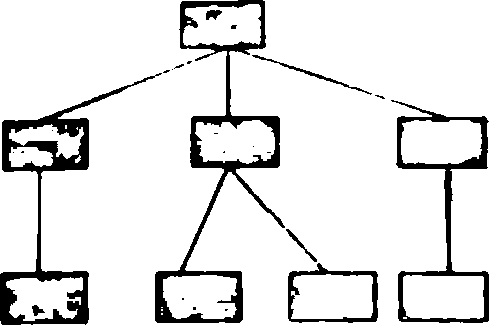
b) Compute the Fenton** Size Metric and the Fenton's Cormccfcvrt} Density Metric for the following Call and Return Architecture.
c) Consider the following Project Data for the evaluation of (fee Afferent Size Oriented
|
7 J ( LfX'J 1 tn prH*n. I I 1 month |
1 -Sc 1 |
Pfrrxr. P8) |
r' |
v >w a |
Noof 1 pert-.. ! |
|
[ALPHA (2002 J 12,000 I 24 1 1 1 |
400 |
150 |
25 |
3 | |
|
kia pmf ujooo tp jo 1 fjf f 1 _ |
12 |
1000 |
250 |
50 |
6 |
|
(2004) 1 1 |
1 |
100 |
175 |
5 |
Study the above table and evaluate the following 4 different types of Size Oriented Metrics:*
a) Errors per KLOC
b) Defects per KLOC
c) Cost per KLOC (Thou)
d) Doc per KLOC
*
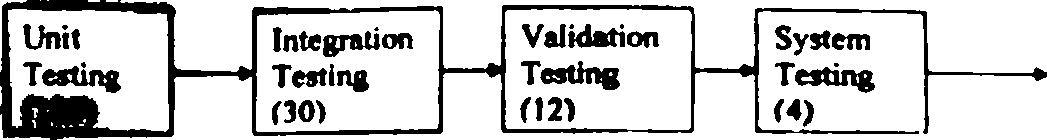
d) The oumber of bugs found during the different testing phases is shown in the following Aagrani while conducting testing activity in a certain testing scenario. Compute the DRE
(Defect Removal Efficiency) for each of the testing phases. It is to be noted that, finally only ooe bug wm found b the customer location
*
|
Attachment: |
| Earning: Approval pending. |
