Uttar Pradesh Technical University (UPTU) 2007 B.E Computer Science COMPUTER NETWORKS - Question Paper
COMPUTER NETWORKS
CS - 602
* V - 1 036*
Printed Pages : 4
(Following Paper ID and Roll No. to be filled in your Answer Book)
|RoI1 No. I I I I I I I I I n B. Tech.
PAPER ID : 1036
(SEM. VI) EXAMINATION, 2007 COMPUTER NETWORKS
Time : 3 Hours] [Total Marks : 100
Note : (1) Attempt all questions.
(2) All questions carry equal marks.
1 Attempt any four parts : 5x4=20
(a) Explain the working principle of optical fibre transmission media. Show how it works :
(i) Multi mode graded index
(ii) Mono mode step index.
(b) What is ISDN? Describe in brief the ISDN working to provide various services.
(c) Answer whether true or false with justification :
(i) Switch breaks the 543 rule for Network topology.
(ii) The maximum length of a cable segment in 10 base T can be 200 meters.
(iii) Entire bandwidth is occupied by a single frequency when using a broadcast data transmission.
(iv) Bridge isolate the two broadcast domains.
(d) A low transmission tower used to transmit data using 3 kHz bandwidth over the link along with
1 Watt of noise power. Calculate the rate of data transmission.
(e) Draw the layer diagram of TCP/IP protocol suit and explain it briefly.
(f) What is meant by terminal handling? Explain it with the help of suitable diagram.
Answer any four of the following : 5x4=20
(a) What are the different types of error detection methods? Explain the CRC error detection technique using generater polynominal
x4 + x3 + 1 and data 11100011.
(b) Describe the stop and wait flow control technique.
(c) Two neighbouring nodes A and B uses sliding window protocol with 3 bit sequence number.
As the ARQ mechanism Go back N is used with window size of 4. Assume A is transmitting and B is receiving show window position for the following events :
(i) Before A send any frame
(ii) After A send frame 0,1,2 and receive ACK (acknowledgement)from B for 0 and 1.
(d) An Aloha network user 19.2 kbps channel for sending message packets of 100 bit long size. Calculate the maximum throughput for pure ALOHA network.
(e) Describe with the help of suitable diagram the Go-back-N continuous RQ error control scheme.
(f) Prove that the throughput of Network using slotted Aloha can be given as
where G is the load and S is throughput.
Answer any four of the following
5x4=20
(a) What is count to infinity problem? How it can be solved using split horizon algorithm? What are its limitations?
(b) Answer the following question :
(i) Why the leaky bucket algorithm allow just one packet per tick, irrespective of packet size?
(ii) Why the reassembly of packets is done at destination instead of intermediate system in Internet?
(c) Explain the following terms with example :
(i) Multicast addressing
(ii) Unicast addressing
(iii) Anycast addressing.
(d) Explain the different types of headers supported by IPr6.
(e) Complete the final routing table at node A using RIP protocol for the following network. Assume the cost of hop count.
|
Distance |
Cost |
Next Hop |
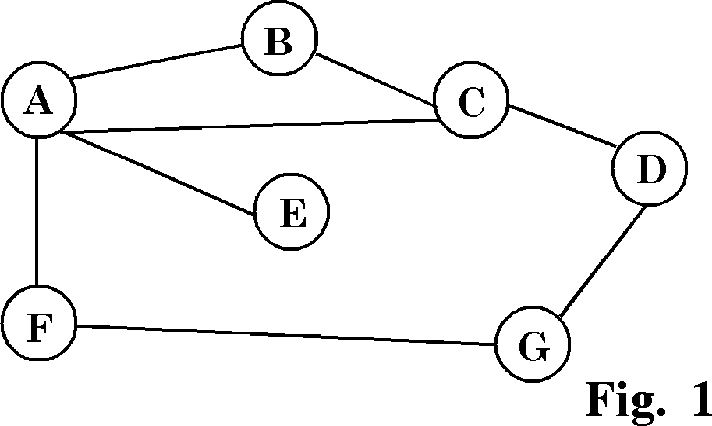
(f) What is meant by congestion in network? Explain the Decbit algorithm for congestion avoidance.
Answer any two of the following : 10x2=20
(i) Explain the message authentication operation used in RSA technique.
(ii) Generate the public key and secret key for the following prime numbers using RSA algorithm : p = 3, Q = 11 take E = 5
(iii) Differentiate between the block cypher with transposition cypher.
(iv) Discuss the RPC design and implimentation issues.
Answer any two of the following : 10x2=20
(a) Answer the following related to DNS :
(i) How does DNS perform name resolution?
(ii) What are the different types of name servers?
(iii) Mention the DNS message format for query and reply messages.
(b) Answer the following related to SMTP :
(i) What are the three main components of internet mail system?
(ii) Give three SMTP commands issued by client and explain it briefly.
(iii) How does the SMTP perform the mail data transfer operation ?
(iv) Give mail message format using multimedia mail extension.
(c) Write short notes on any two of the following :
(i) FTP and TFTP
(ii) Virtual private networking
(iii) Firewall.
V-1036] 4 [ 1460 ]
|
Attachment: |
| Earning: Approval pending. |
